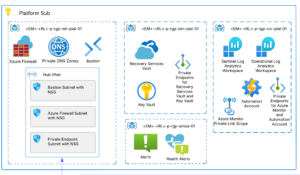
What is Azure Web Application Firewall (WAF)?
Azure Web Application Firewall (WAF) filters, monitors, and blocks HTTP traffic. It uses Open Web Application Security Project® (OWASP) rules to protect your application. It also provides centralized protection to web applications from common exploits and vulnerabilities and protects against threats and intrusions.
Supported Services
We have three different options to create a WAF in Azure:
- Azure Front Door: Global, scalable entry-point that uses the Microsoft global edge network to create fast, secure, and widely scalable web applications.
- Azure Content Delivery Network (CDN): Global CDN solution for delivering high-bandwidth content. It can be hosted in Azure or any other location.
- Azure Application Gateway: Web traffic load balancer that enables you to manage traffic to your web applications.
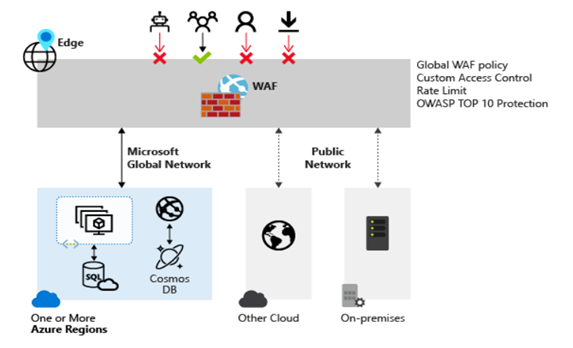
Azure Front Door
Azure Front Door provides centralized protection for our web applications. It prevents malicious attacks close to the attack sources before they enter your virtual network.
As shown in the below image, we placed WAF at Azure network edge locations. It will inspect every incoming traffic, so it will prevent malicious attacks from entering the virtual network.
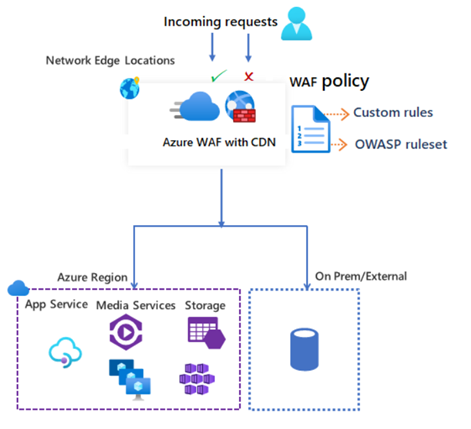
Azure Content Delivery Network (CDN) Service from Microsoft
Azure Content Delivery Network (CDN) provides a global and centralized solution for our web content. It will reduce load times, bandwidth, and speed responsiveness of the application.
As shown in the image, WAF deployed on Azure network edge locations around the globe. A WAF policy easily links to any CDN endpoint in your subscription. New rules can be deployed within minutes and respond quickly to changing threat patterns.
Azure Application Gateway WAF
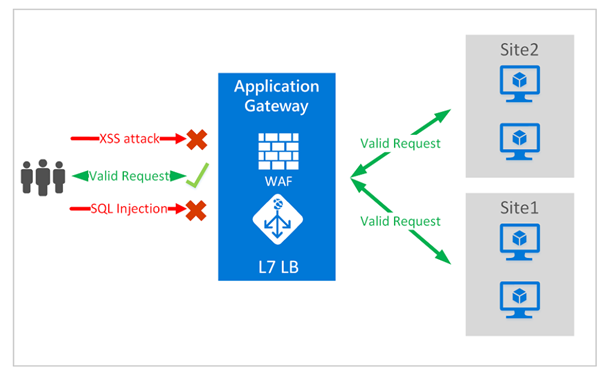
Application security is strengthened by WAF integration into Application Gateway. Protect your web applications from web vulnerabilities and attacks without modification to back-end code. We can protect multiple web applications at the same time. An instance of Application Gateway can host up to 40 websites protected by a web application firewall. In addition, we can custom WAF policies for different sites behind the same WAF. As shown below, we can also Protect our web applications from malicious bots and XSS attacks, SQL Injection, and other vulnerabilities by using Application Gateway WAF.
WAF Modes
WAF policy can be configured to run in the following two modes:
- Detection mode: When running in detection mode, WAF doesn’t take any actions other than monitoring and logs the request and its matched WAF rule to WAF logs.
- Prevention mode: In prevention mode, WAF takes the specified action if a request matches a rule. If a match is found, no further rules with lower priority are evaluated. Any matched requests are also logged in the WAF logs.
WAF Policy and Rules
WAF policy consists of two types of security rules:
- Custom rules that are authored by the customer
- Managed rule sets that are a collection of Azure-managed pre-configured set of rules
Custom rules are reviewed before processing the rules in a managed rule set. A rule is made of a match condition, a priority, and action. If such a match is processed, rules with lower priorities aren’t processed. We can create rules that meet our requirements by combining managed and custom rules. For example, we can configure custom rules based on IP address, Geographical location, HTTP parameters, size constraint, rate limiting.
WAF Actions
WAF customers can choose to run from one of the actions when a request matches a rule’s conditions:
- Allow: Request passes through the WAF and is forwarded to the back-end. No further lower priority rules can block this request.
- Block: The request is blocked, and WAF responds to the client without forwarding the request to the back end.
- Log: Request is logged in the WAF logs, and WAF continues evaluating lower priority rules.
- Redirect: WAF redirects the request to the specified URI. The URI specified it is a policy-level setting. Once configured, all requests that match the Redirect action will be sent to that URI.
WAF Monitoring
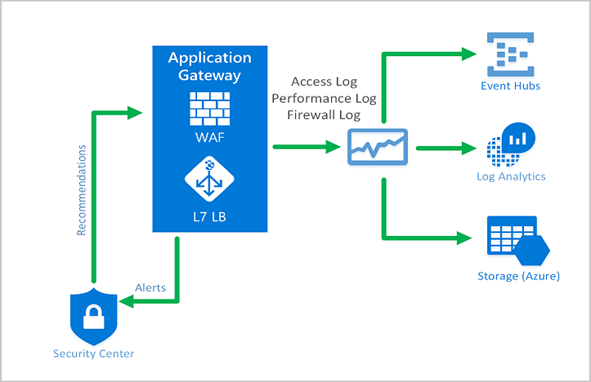
Monitoring the health of your WAF and the applications that it protects is supported by integration with Azure Security Center, Azure Sentinel, and Azure Monitor logs. WAF instances are integrated and send alerts and health information to Security Center for reporting. Azure Monitor allows us to track diagnostic information, including WAF alerts and logs.
How To Deploy Azure Web Application Firewall (WAF) with Azure Application Gateway
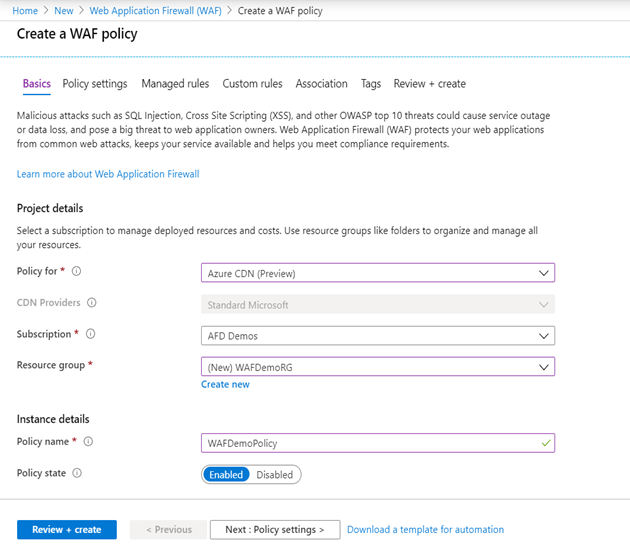
- Create WAF Policy to configure the firewall. Search Web Application Firewall Policy click and Add policy. Then we need to select the type of WAF, Resource Group, Policy Name, and state.
Reference – https://docs.microsoft.com/en-us/azure/web-application-firewall/cdn/waf-cdn-create-portal - Select Prevent or Detect mode based on the requirement.
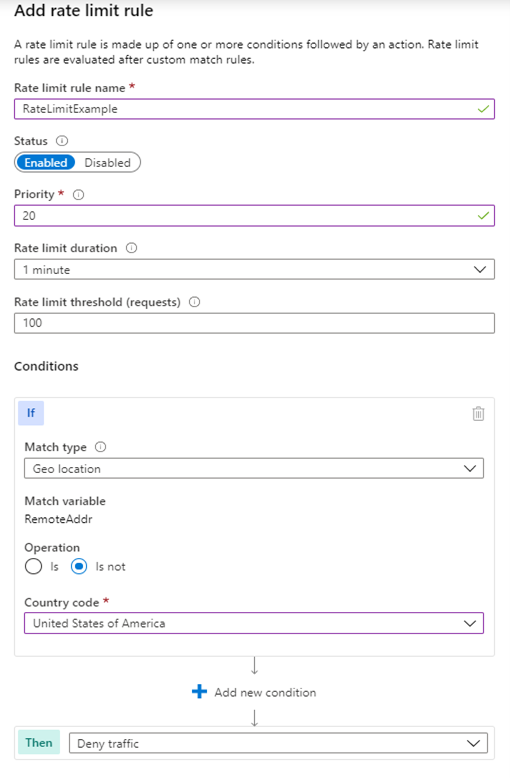
- We can configure a custom rules section to match the rule and rate limit rules. As shown in the image below, we can limit the threshold value and duration.
- Review your settings, then create!
Conclusion
All organizations are exposed to a variety of malicious attacks. To protect from such, we can use Azure WAF to protect the application even from the most sophisticated threats before they reach your servers. To learn more, check out Microsoft documentation on Azure WAF or reach out to AIS.
SECURE YOUR CLOUD SOLUTIONS
Your cloud adoption efforts require sound security, compliance, and governance. It is our mission to make those requirements a reality. Contact AIS about our Security and Compliance Consulting Services.