Cloud Application development has blown up to the point that it has increased the vital need for enterprise mobility and security solutions to manage people, devices, apps, and data for all organizations’ sizes. Additionally, the pandemic has led to businesses’ need to increasingly offer remote working options that facilitate employees to use their personal or company-owned devices. Therefore, enterprise mobility management and security solutions will have a long-term impact in the future.
Governance and compliance regulations are the biggest challenges when choosing a suitable and sturdy solution. This is where Microsoft’s Enterprise Mobility and Security solution acts to provide a more significant transformation of the workloads with identity and access management, endpoint management, information protection, and security through various Microsoft 365 policies configurations. This article explains how these policies are scattered under Enterprise Mobility and Security solution as follows.
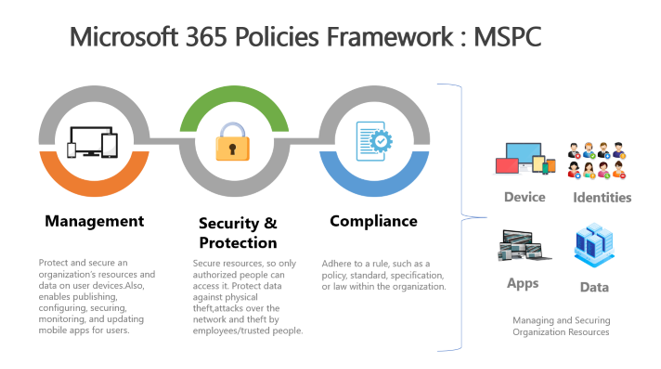
Microsoft 365 policies are continuously evolving to protect organization resources such as devices, apps, identities, and data. I categorize these policies into three significant blocks and refer to them as a whole as Microsoft 365 Policies Framework – MSPC. Let us walk through the unique features of all these components.
Management
The Management aspect of the Enterprise Mobility and Security solution provides easy and secure access of devices or apps to users with Microsoft 365 licenses when collaborating with people inside or outside the organizations, regardless of any locations or types of devices. It comes with a centralized place to Secure, deploy, and manage all users, apps, and devices called Microsoft Endpoint Manager.
Microsoft Endpoint Manager is designed to help administrators use Configuration Manager and Intune together with cloud-only or hybrid setup for devices and apps management. This management process comes with Microsoft Intune, which includes Mobile Device Management (MDM) and Mobile Application Management (MAM) providers with different policies to configure and control the devices and apps once they are enrolled as follows. MDM controls employees’ corporate and personal devices, while MAM manages data and privacy within the apps and devices.
MDM Policies
- Device Configuration Profiles: Devices profiles policies let you configure settings and then push these settings to devices in your organization. We can apply these settings to both devices and users. If settings are configured for devices, it remains with the device, regardless of who is signed in. If settings are configured for users, then it goes with the user when signed into their devices.
- Device Compliance policies: This policy provides rules and settings that users and devices must meet to be compliant with organization standards for the devices, such as OS platform or security feature in the device. When a compliance policy is deployed to a user, all the user’s devices are checked for compliance. And as an Administrator, you can remotely lock/retire the devices if a device is not compliant for the user or notify them.
- Device Conditional Access Policies: To enforce the access requirements of users, based on specific conditions such as unfamiliar sign-in, User or group, IP Location, Users with devices of particular platforms, conditional access policies are used. When these conditions are matched, conditional access policies direct users to perform certain actions such as password changes, multi-factor authentication, or as an administrator, you can block access or grant access.
MAM Policies
- App Configuration policy: It provides the ability to publish configuration settings for iOS/iPad and Android apps. For example, As an Administrator, you can change custom port numbers, Language settings, Security settings, Branding settings such as a company logo of the applications removes the user’s involvement to configure the application on their own.
- App Protection Policy: App protection policy is applied to the app, such as desktop/Mobile apps for any managed or unmanaged devices. This policy is used to ensure an organization’s data safety, making the app a managed app. It provides a rule that is enforced when the user attempts to access or move “corporate” data or a set of prohibited or monitored actions when the user is inside the app. For example, As an Administrator, you can restrict copy-paste action between certain apps or print organization data.
- Office App Policy: Many policies are meant for Office apps only to add to Microsoft Intune and apply to groups of end-users. For example, blocking add-ins in Excel, disabling the shortcut keys in Word, clearing cache on close, or even hyperlink color in documents. Currently, there are 2093 policies to apply across multiple platforms for office applications.
Security & Protection
“Security and Protection” is a crucial component of Microsoft 365 policies, configurable from the portals such as Microsoft Security Center, Microsoft Cloud App Security Center, Microsoft Defender Security Center, Microsoft Defender for Identity, and Azure Portal. These portals help detect, prevent, investigate, and respond across endpoints, identities, email, and applications to provide integrated protection against sophisticated attacks.
Microsoft Defender for Office 365
It is a place where you can see risky users. Incident reports such as impossible travel activity, security score with recommended actions, and the ability to create an advanced custom query to identify security breach activity against schema such as generated alerts/apps/identities/devices/threat activities. It safeguards the organization against malicious threats posed by email messages, links (URLs), and collaboration tools. Moreover, you can also create threat protections policies explained as follows:
- Anti-malware policy: As an Administrator, you can quarantine the message for your review if malware is detected in an attachment. Thereby, you can block attachment types in an email that may harm the computer.
- Anti-phishing Policy: This policy allows to configure anti-phishing protection settings for a specific group of users over emails to avoid malicious attacks based on impersonation to steal sensitive information from the messages. As an administrator, you can configure an action if a malicious email is found, such as redirecting the message to decision-makers or quarantine the message or delete the message.
- Safe attachment policy: It is an extra layer of security on top of the Exchange online protection for the inbound messages as well as files residing in the SharePoint, OneDrive, and teams. Using this policy, administrators can investigate malicious attachments or files that could destroy user data/steal information.
- Domain Keys Identified Mail: This policy configuration helps protect both senders and recipients from hackers to forge email in transit.
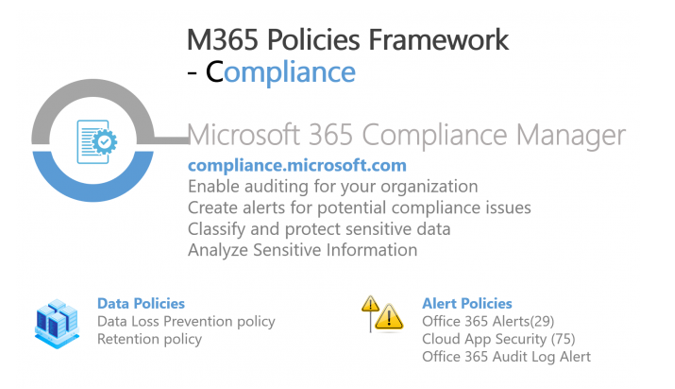
Further, you can also configure 29 default alert policies that help identify Exchange admin permissions abuse, malware activity, potential external and internal threats, and information governance risks.
Microsoft Cloud App Security (MCAS)
Cloud App Security portal is a comprehensive solution to investigate on-premises logs and cloud content such as files/user accounts. It provides a rich visibility control over data and sophisticated analytics to identify and resolve cyber threats across all cloud services. The whole office 365 usage logs are ingested in cloud app security for better visibility and alert configurations. Office 365 usage log activities are available based on conditional access and app configuration in the Cloud app security. At present, there are 75 inbuilt configurable alert policies to generate email notifications for specified users on suspicious activities. You can also investigate all security configuration gaps across multi-cloud platform such as AWS/Azure/Google. In the CAS portal, you can view recommended actions to improve the identity security posture, for example, stopping clear text credentials exposure. Additionally, as an Administrator, you can create policies as follows:
- Access policy: It generates an alert or grant access based on a match of certain devices/apps/users.
- Activity policy: It helps notify the concerned user on mass download, multiple failed user log-on/log on from risky machine/browser. It also allows to create an alert based on any usage activity occurred in Microsoft 365.For example, Notify decision makers by configuring an alert in the Activity policy, when DLP policy in Power Platform has changed.
- App discovery policy: It helps generate alerts when new apps are discovered in your organization.
- Cloud discovery anomaly detection policy: It creates an alert based on compliance, security, or general risk factors such as HIPAA, ISO 27001, data center, domain, GDPR, etc. and unusual increases in cloud application usage such as downloaded data, uploaded data, transactions, and users are considered for each cloud application. For example, trigger alert for the top three suspicious activities per 2,000 users per week.
- File policy: It generates an alert if the File is shared with a personal email or unauthorized domain. Based on this alert, the Administrator can further remove a user or apply a protection label or put the user in quarantine.
- Oauth app policy: This policy helps generate an alert if the app matches specific permission levels or permission requests. As an Administrator, you can also revoke permissions for the app user who authorized it. For example, you can automatically be alerted when apps require a high permission level and were authorized by more than 30 users.
- Session policy: Session policy provides real-time monitoring and control over user activity in the cloud apps. For example, As an Administrator, create a session policy to monitor Power BI activities.
Microsoft Defender for Endpoint (MDE)
Microsoft Defender for Endpoint is a complete solution to help enterprise networks monitor and respond to threat activity. It continuously discovers the threats and detects a vulnerability, and suggests remediation. It provides security configuration posture of organizations devices across OS, Application, Network, Accounts, and Security Controls. These activities are observed via the sensor installed in the domain controller. You can view a dashboard that summarizes threat activities such as the latest and positively impacted threats or threat impacts over the organization.
With Microsoft Defender for Endpoint, As an Administrator, you can assess your organization’s impact, review security resilience and posture – for example, charts that provide an overview of how resilient your organization is against a given threat. It also suggests the recommended actions that can help you increase your organizational resilience against the threat and eventually, the security posture.
Microsoft Defender for Identity (MDI)
Microsoft Defender for Identity is one of the Microsoft Defender suit components used to detect and investigate advanced threats, compromised user accounts, and malicious insider actions directed in the organization based on on-premises active directory activities.
MDI monitors and analyzes user activities and information across the enterprise network. It learns about user behavior by identifying user permissions and detects suspicious activities to provide deep insights. It helps to reveal the advanced threat activities, compromised user accounts, and insider threats facing your organization. It also helps to provide hybrid attacks on ADFS.
Azure Portal for Identity Protection
The Azure portal allows configuring policies for identity protections that help Automate the detection and remediation of identity-based risks such as leaked credentials, authentication by a different user, or unfamiliar activities such as accessing an anonymous app IP address, impossible travel, etc. These are the default policies that administrators can configure.
- Azure AD MFA registration policy: This policy act as a self-remediation method for risk events within Identity Protection. It is a process where a user is prompted at the sign-in process for an additional identification form. This could be to enter a code on their cellphone or to provide a fingerprint scan. It is also used to roll out Azure AD Multi-Factor Authentication (MFA) via Conditional Access policy.
- Sign-in risk policy: This policy block/allow access or allow access but require multi-factor authentication to users based on the user risk level. This risk level is analyzed from each sign-in, both real-time and offline. It is based on the sign-in activity only and analyses the probability that the user may not have performed the sign-in.
- User risk policy: This policy block/allow access or allow access but require a password reset to users based on the user risk level. This risk level is analyzed from each sign-in, both real-time and offline. It detects the probability that a user account has been compromised by detecting risk events that are atypical behavior of a user.
Compliance
Microsoft compliance manager helps to manage risks and protect data from aligning with industry standards. It also provides visibility on the current level of enterprise compliance posture and suggests recommended actions to improve. It is majorly used to classify and protect sensitive information and generates alerts if any compliance issues are detected. You can enable the auditing for entire Microsoft 365 workloads. There are three central policies that you can configure from the compliance manager as explained follows:
- Data loss prevention policy: DLP policy for Microsoft 365 workloads to help identify and protect the organization’s sensitive information. For example, as an administrator, you want to prevent users from sending email messages that contain specific credit card numbers or sensitive information about projects/businesses.
- Retention policy: with increasing data every day, governing data is a crucial task to comply with industry regulations and internal policies, reduce the security breach and improve productivity. As an administrator, you can retain the content forever or for a specified time or delete the content after a specified time by creating a retention policy.
- Audit log alert policy: As an administrator, you can create alerts based on user activities that match the alert policy’s condition. For example, you can create an alert when the user modifies the Power Platform’s DLP policy. There is almost 500+ activities based on which you can generate the alert and notify respective users.
In essence, Enterprise Mobility and Security is a foundation to keep organization assets safe, whether in the cloud, on-premises, or in a hybrid setup. Properly setting up this ecosystem of policies require a driven mindset and strong command of different tools and features. I hope this article helps to spark more ideas and interest to move forward to build a deeper understanding of mobility and security aspects and ultimately lead to more robust security postures.
To get started with Microsoft Mobility and Security learning, I suggest subscribing to the Microsoft 365 Development program and building the test environment to configure various Mobility and Security scenarios via Microsoft 365 policies. This would also provide experience towards earning “Microsoft 365 Certified Enterprise Administrator” certification. See the links below to get started:
Step 1:
- Join Microsoft 365 Developer Program: https://developer.microsoft.com/en-us/microsoft-365/dev-program
Step 2:
- Build Test Environment – https://docs.microsoft.com/en-us/microsoft-365/enterprise/m365-enterprise-test-lab-guides?view=o365-worldwide
Step 3:
- Microsoft Endpoint Manager – https://www.microsoft.com/en-us/microsoft-365/microsoft-endpoint-manager
- Identity Protection – https://docs.microsoft.com/en-us/azure/active-directory/identity-protection
- Microsoft Defenders – https://docs.microsoft.com/en-us/microsoft-365/security/mtp/microsoft-threat-protection?view=o365-worldwide&WT.mc_id=Portal-Microsoft_Azure_Support
- Microsoft Compliance – https://docs.microsoft.com/en-us/microsoft-365/compliance/compliance-quick-tasks?view=o365-worldwide
- Alert Policies – https://docs.microsoft.com/en-us/microsoft-365/compliance/alert-policies?view=o365-worldwide#default-alert-policies
- Microsoft 365 Security Roadmap – https://docs.microsoft.com/en-us/microsoft-365/security/office-365-security/security-roadmap?view=o365-worldwide
- Technical Guidance on Security – https://docs.microsoft.com/en-us/security
Step 4:
- Enterprise Administrator Expert Certification – https://docs.microsoft.com/en-us/learn/certifications/m365-enterprise-administrator