If you’re looking for an intelligent cloud-native Security Information and Event Management (SIEM) solution that manages all incidents in one place, Azure Sentinel may be a good fit for you. We’ll be walking through what is Azure Sentinel and how your organization can use it to enhance your data capabilities.
What is Azure Sentinel?
Not only does Azure Sentinel provide intelligent security analytics and threat intelligence, but it’s also considered a Security Orchestration and Automation Response (SOAR) solution, meaning it will collect data about security threats and you can automate responses to lower-level security events without the traditionally manual efforts required. You can extend this solution across data sources by integrating Azure Sentinel with enterprise tools, like ServiceNow. There are also services offered at no additional cost, such as User Behavior Analysis (UBA ), Petabyte daily digestion, and Office 365 data ingestion, to make Azure sentinel even more valuable.
BETTER SECURITY FOR YOUR CLOUD
We'll help you review your current security posture, risks, and gaps to establish a secure code culture. Reach out today to learn more.
First Impression
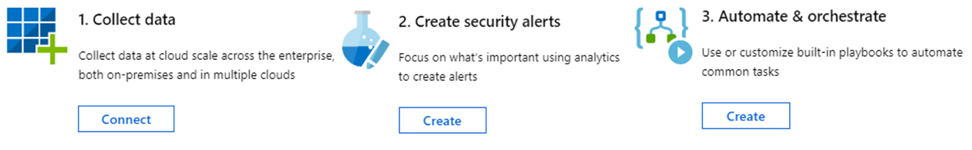
After opening Azure Sentinel from the Azure portal, you will be presented with the below items:
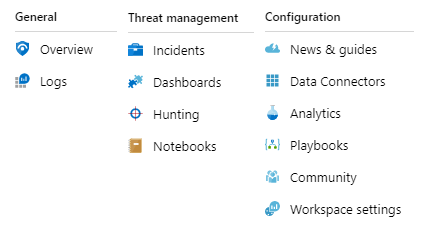
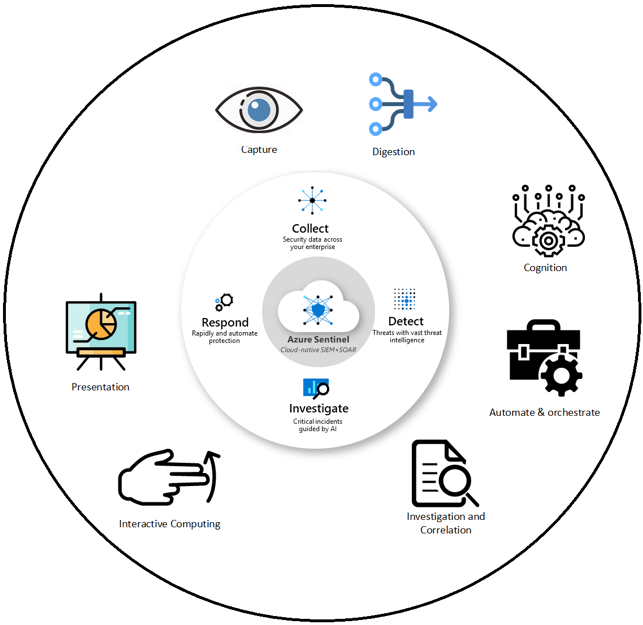
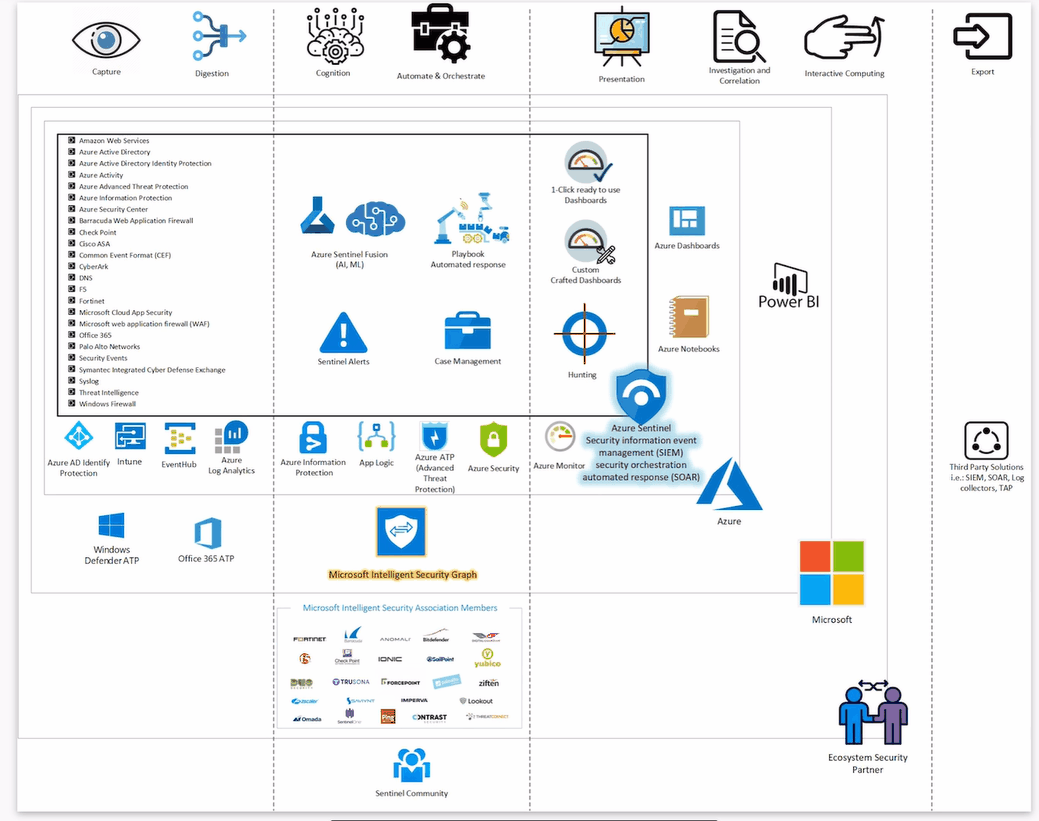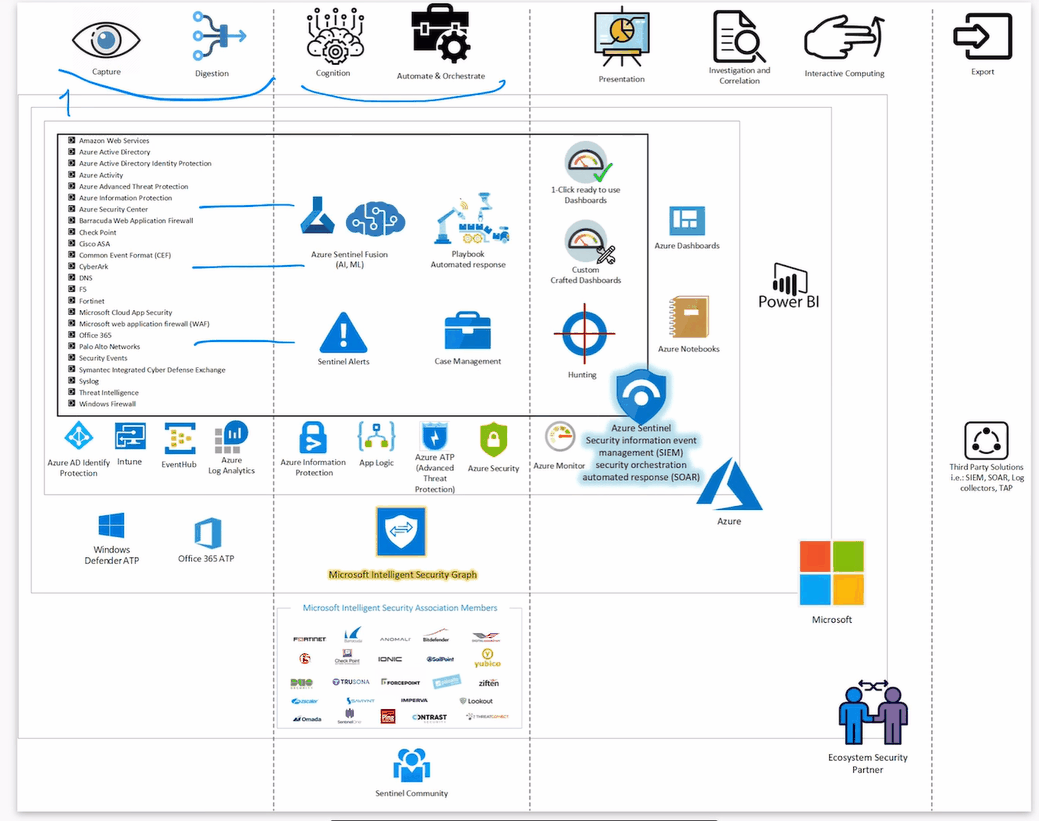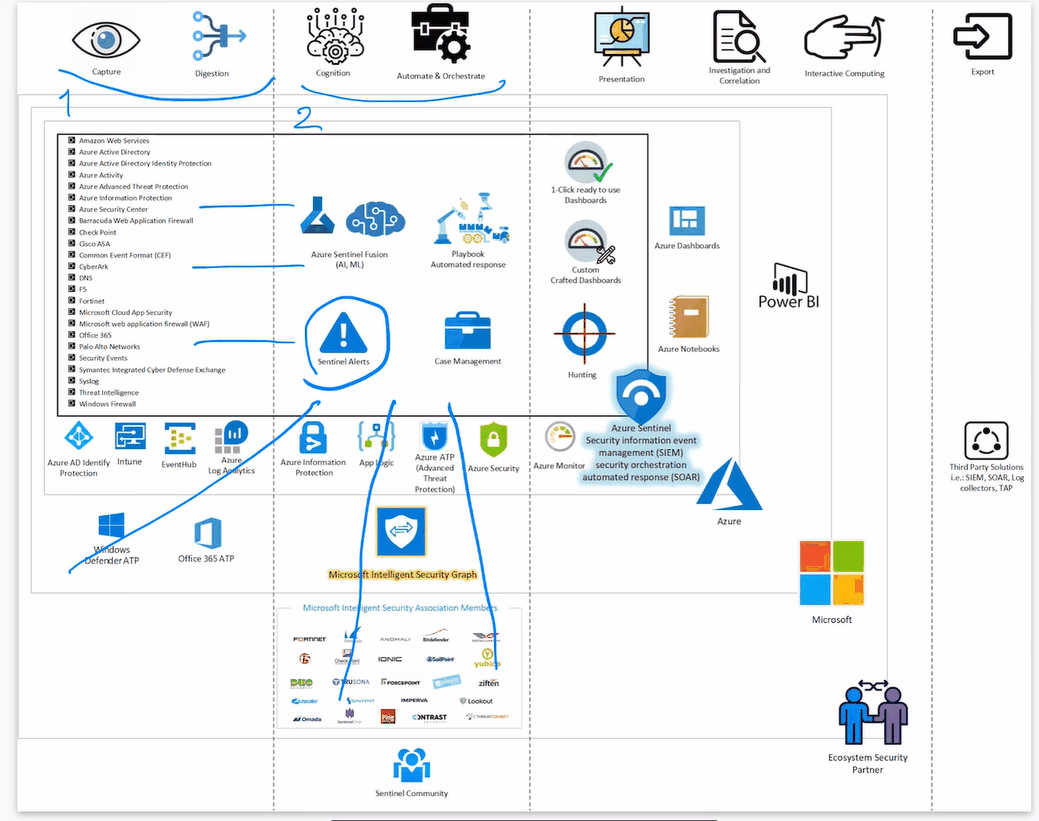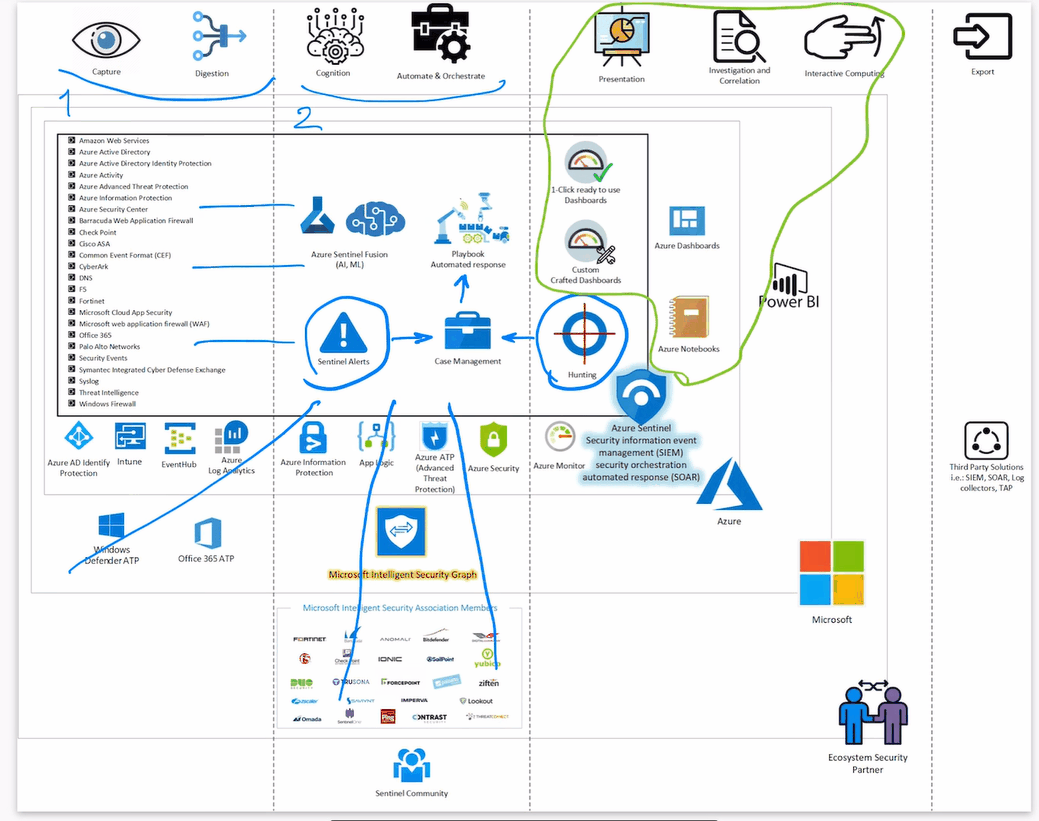
Theoretically, Azure Sentinel has four core areas.
- Collect – By using connections from multiple vendors or operating systems, Azure Sentinel collects security events and data and keeps them for 31 days by default. This is extendable up to 730 days.
- Detect – Azure Sentinel has suggested queries, you can find samples, or build your own. Another option is Azure Notebook, which is more interactive and has the potential to use your data science analysis.
- Investigate – For triaging using the same detection methodology in conjunction with events investigation. Later you will have a case created for the incident.
- Respond – Finally, responding can be manual or automated with the help of Azure Sentinel playbooks. Also, you can use graphs, dashboards, or workbooks for presentation.
For a better understanding, the flow in this example of behind the scene is helpful.
How do I enable Azure Sentinel?
If you already have an Azure Log Analytics Workspace, you are one click away from Azure Sentinel. You need to have contributor RBAC permission on the subscription that has Azure Log Analytics Workspace, which Azure Sentinel will bind itself to it.
Azure Sentinel has some prebuilt dashboards and you are able to share it with your team members.
You can also enable the integration of security data from Security Center > Threat Detection > Enable integration with other Microsoft security services
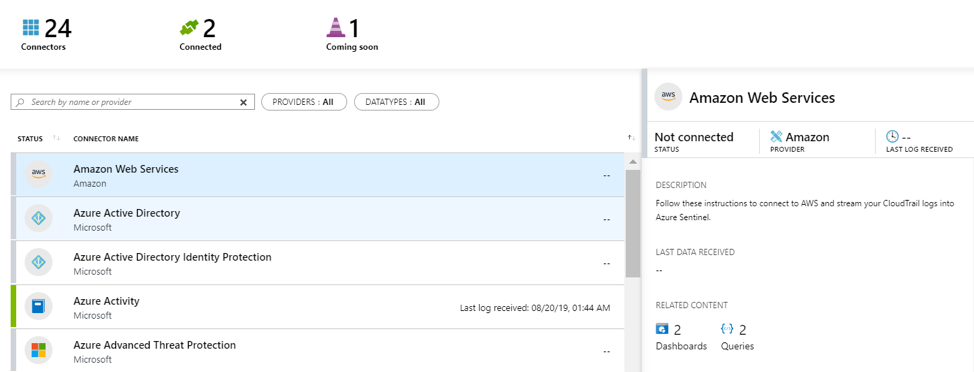
Now, let’s talk Azure Sentinel data sources. They have a variety of built-in connectors that collect data and process it with its artificial intelligence empowered processing engine. Azure Sentinel can relate your events to well-known or unknown anomalies (with the help of ML)!
Below is a sample connection which offers two out-of-the-box dashboards:
All connections have a fair amount of instructions, which usually allows for a fast Azure Sentinel integration. A sample of an AWS connector can be found here.
Azure Sentinel has thirty out-of-the-box dashboards that make it easy to create an eloquent dashboard, however, built-in dashboards only work if you have configured the related connection.
Built-In Ready to Use Dashboards:
- AWS Network Activities
- AWS User Activities
- Azure Activity
- Azure AD Audit logs
- Azure AD Sign-in logs
- Azure Firewall
- Azure Information Protection
- Azure Network Watcher
- Check Point Software Technologies
- Cisco
- CyberArk Privileged Access Security
- DNS
- Exchange Online
- F5 BIG-IP ASM F5
- FortiGate
- Identity & Access
- Insecure Protocols
- Juniper
- Linux machines
- Microsoft Web Application Firewall (WAF)
- Office 365
- Palo Alto Networks
- Palo Alto Networks Threat
- SharePoint & OneDrive
- Symantec File Threats
- Symantec Security
- Symantec Threats
- Symantec URL Threats
- Threat Intelligence
- VM insights
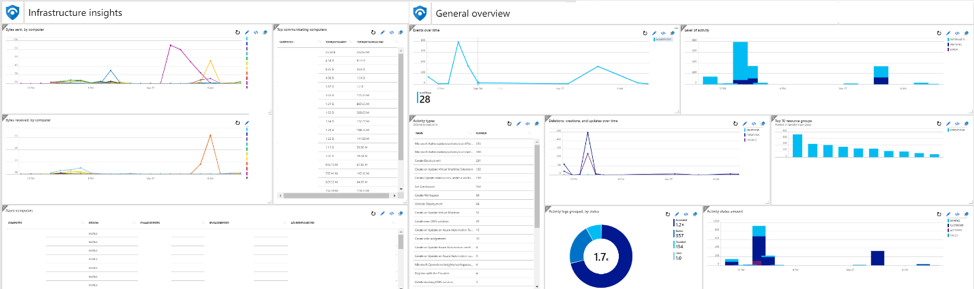
A Sample Dashboard:
One of the most useful IaaS monitoring services that Azure provides is VMInsights, or Azure Monitor for VMs. Azure Sentinel has a prebuilt VMInsight Dashboard. You can connect your VM to your Azure Log Analytics Workspace, then enable VMInsights from VM > Monitoring > Insights. Make sure the Azure Log Analytics Workspace is the same one that has Azure Sentinel enabled on it.
Creating an alert is important. Alerts are the first step for having a case or ‘incidents’. After a case is created based on the alert, then you can do your investigation. For creating an alert, you need to use the KQL language that you probably already used it in Azure Log analytics.
Azure Sentinel has a feature named entity mapping, which lets you relate the query to values like IP address and hostname. These values make the investigation much more meaningful. Instead of going back and forth to multiple queries to relate, you can use entities to make your life easier. At the time of writing this article, Azure Sentinel has four entities; Account, Host, IP address, and Timestamp, which you can bind to your query. You can enable or disable an alert or run it manually as you prefer easily from Configuration > Analytics. Naming might be a little bit confusing since you also need to create your alerts from Analytics.
Azure Sentinel Investigation map of entities becomes public in September 2019 and you no longer need to fill out a form request access.
Let’s Go Hunting
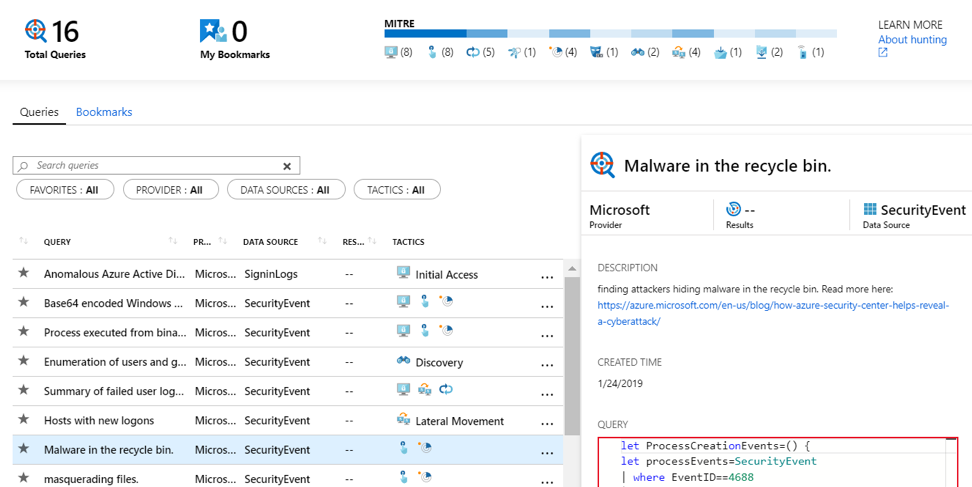
You can use Azure Sentinel built-in hunting queries. You can also directly shoot it down if you know where to find the anomalies by KQL queries and create an alert. Or uses Azure Notebook for AI, ML-based hunting. You can bring your own ML model to Azure Sentinel. Azure Sentinel Notebook is for your tier 4 SOC analysis.
Azure Sentinel uses MITRE ATT&CK-based queries and introduced eight types of queries, also known as bookmarks, for hunting.
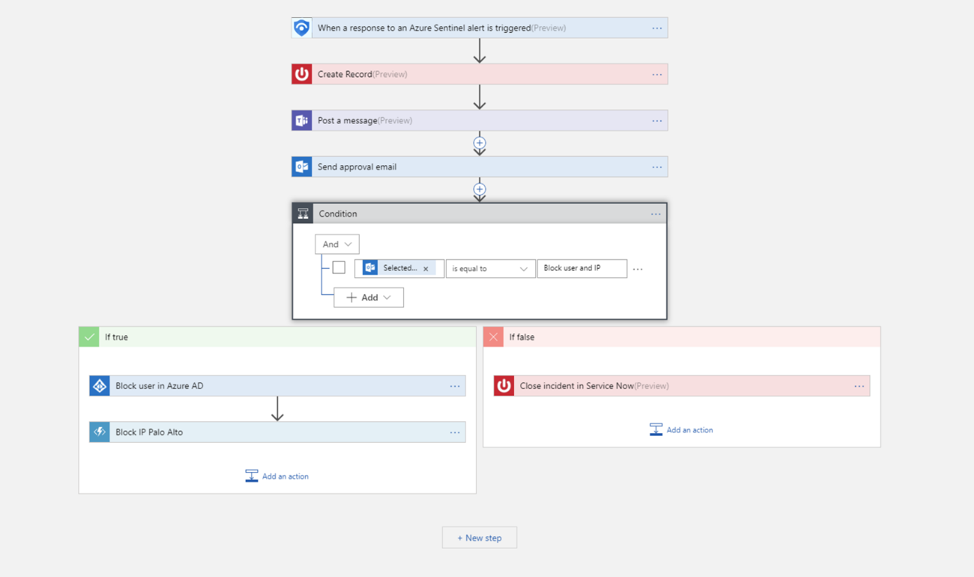
After you become skilled in detection, you can start creating your playbook constructed on logic app workflows. You can also build your automated responses to threads or craft custom actions after an incident has happened. Later you can enable Azure Sentinel Fusion to associate lower fidelity anomalous activities to high fidelity cases.
A sample playbook:
Image Source: Microsoft
Azure Notebooks is a Jupyter notebook (interactive computational tool) for facilitating your investigation by using your data science skills. Azure Notebooks support languages and packages from Python 2 and 3 you can also use R and F#.
We all love community-backed solutions. You can share your findings and designs with others and use their insights by using the Azure Sentinel Community on GitHub.
Azure Sentinel Fusion
Fusion helps reduction of noise by preventing alert fatigue. Azure Sentinel Fusion uses this insight here, and you can see how to enable Azure Sentinel Fusion.
Traditionally we assume an attacker follows a static kill chain as the attack path or all information of an attack is present in the logs. Fusion can help here by bringing probabilistic kill chain and to find novel attacks. You can find more information on this topic here. Formerly, you should run a PowerShell command to enable Fusion, but going on Fusion is enabled by default.
Azure Sentinel Data Sources
Azure Sentinel data sources include three types of connectors. First, Microsoft services are connected natively and can be configured with a few clicks. Second, is by connecting to external solutions via API. And finally, connecting to external solutions via an agent. These connectors are not limited to the below table, and there are some examples of IoT and Azure DevOps that can communicate with Azure Sentinel.
| Microsoft services | External solutions via API | External solutions via an agent |
| Office 365 | Barracuda | F5 |
| Azure AD audit logs and sign-ins | Symantec | Check Point |
| Azure Activity | Amazon Web Services | Cisco ASA |
| Azure AD Identity Protection | Fortinet | |
| Azure Security Center | Palo Alto | |
| Azure Information Protection | Common Event Format CEF appliances | |
| Azure Advanced Threat Protection | Other Syslog appliances | |
| Cloud App Security | DLP solutions | |
| Windows security events | Threat intelligence providers | |
| Windows firewall | DNS machines | |
| DNS | Linux servers | |
| Microsoft web application firewall (WAF) | Other clouds |
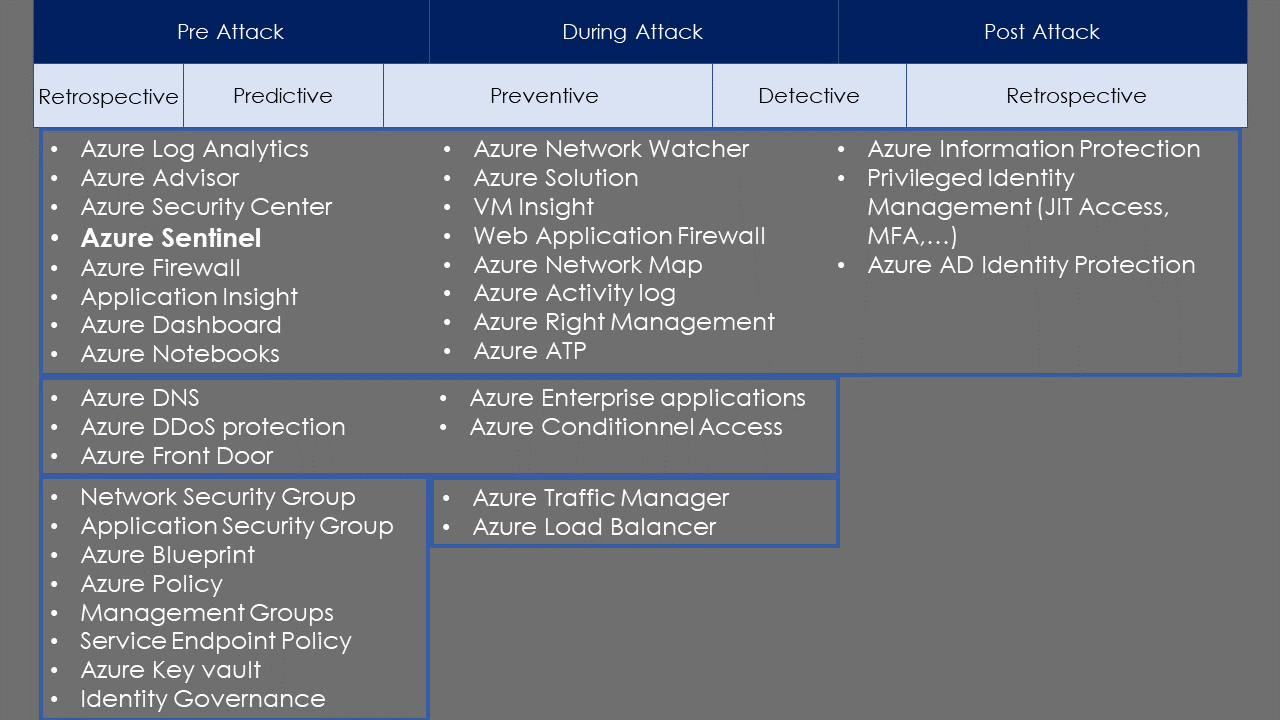
Where Does Azure Sentinel Sit in the Azure Security Picture?
Azure Sentinel can be used before an attack, like Azure Active Directory signings from new locations. During an attack, like malware in the machine or post-attack for investigation about an incident and perform triage with it. Azure Sentinel has a service graph that can show you the related event to an incident.
If you are security titled a person or part of the SOC team and you prefer a cloud-native solution, Azure Sentinel is a good option.
Security Providers or Why Azure Sentinel?
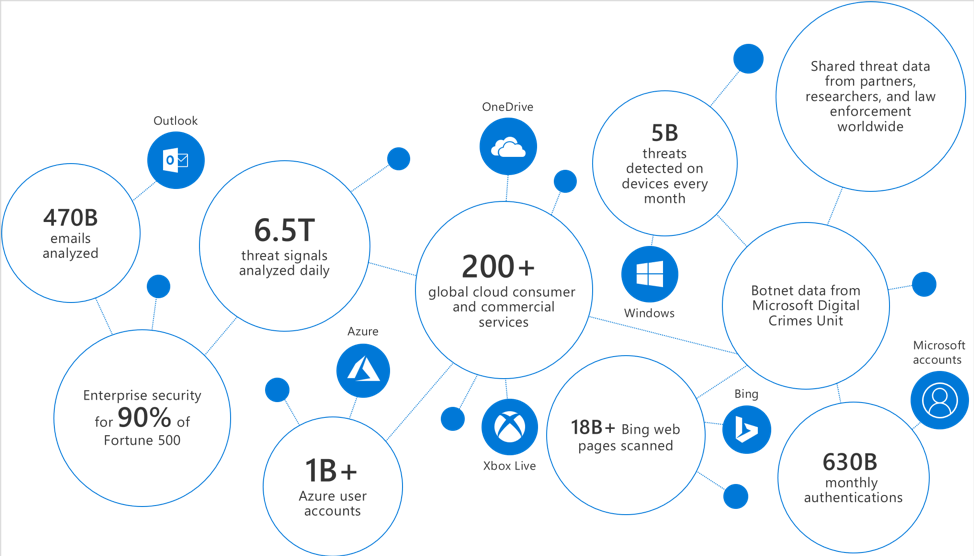
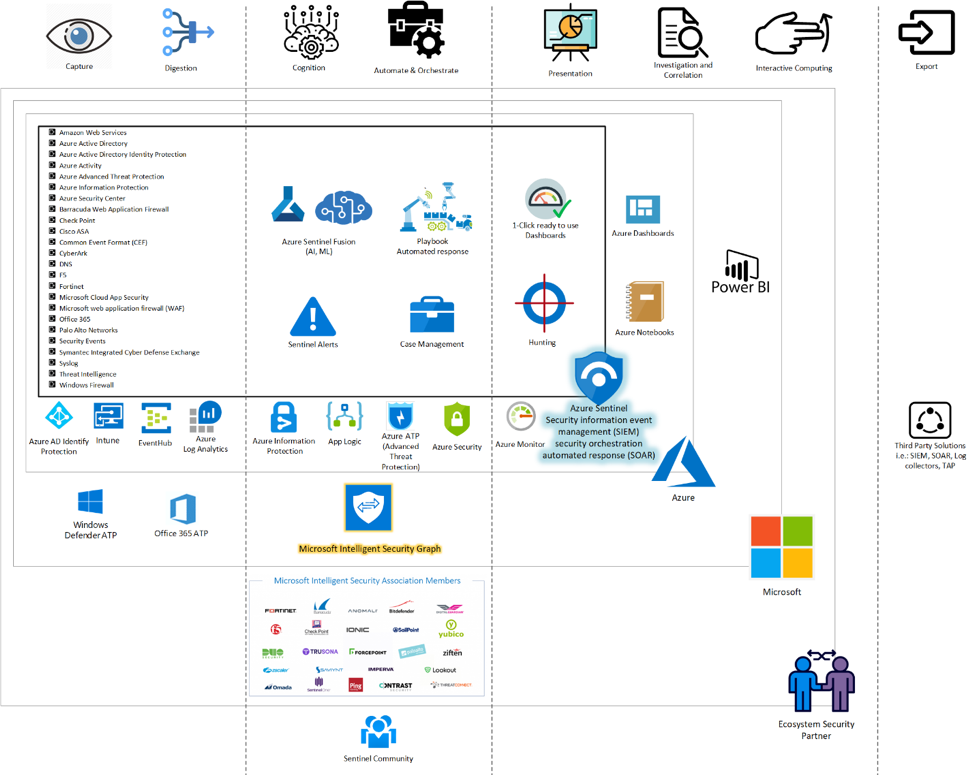
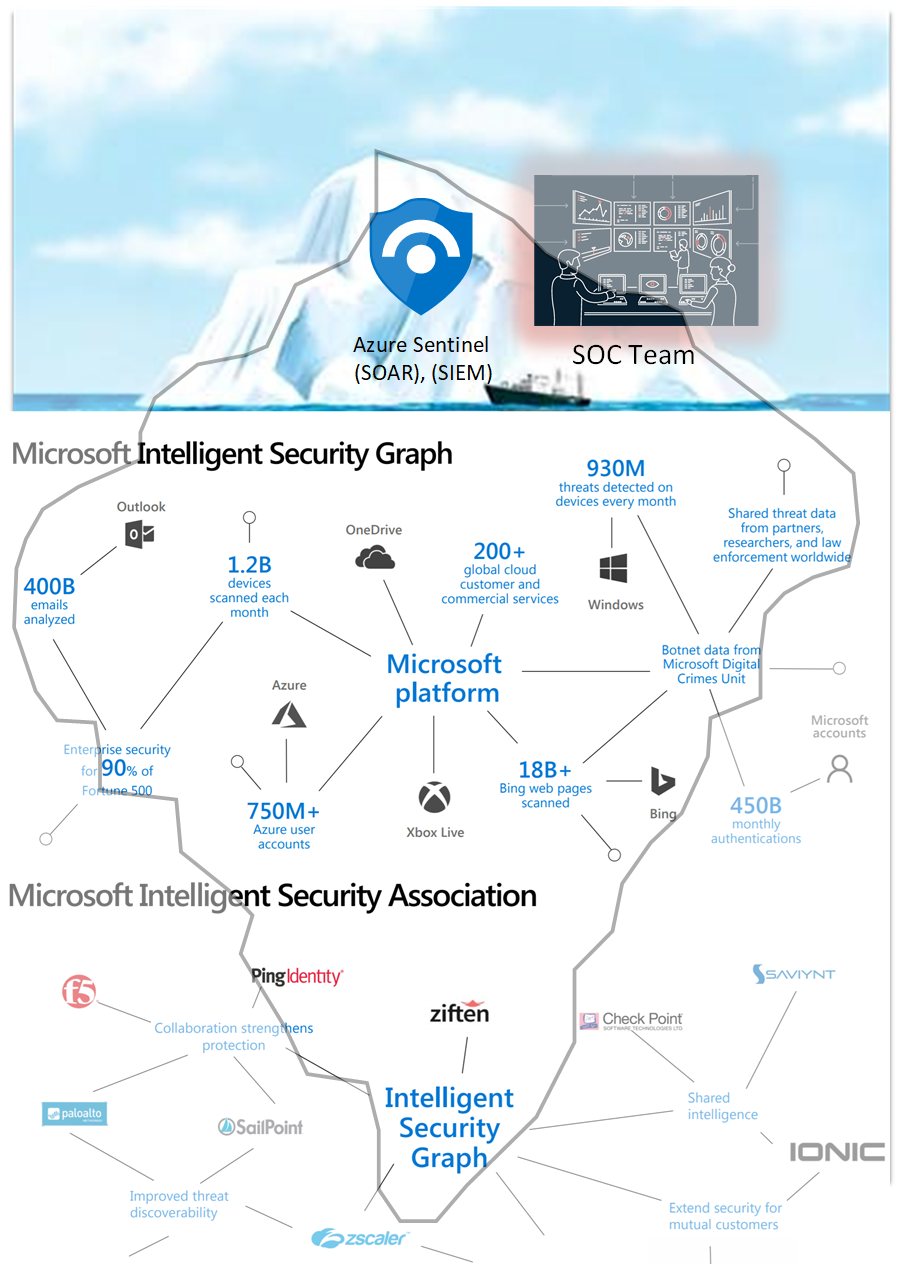
Azure Sentinel uses Microsoft Intelligent Security Graph that is backed by Microsoft Intelligent Security Association. This association consists of almost 60 companies that hand in hand help to find vulnerabilities more efficiently.
Microsoft brings its findings from 3500+ security professionals, 18B+ Bing page scans per month, 470B emails analyzed per month, 1B+ azure account 1.2B devices updated each month, 630B authentications per month, 5B threats blocked per month.
Image Source: Microsoft
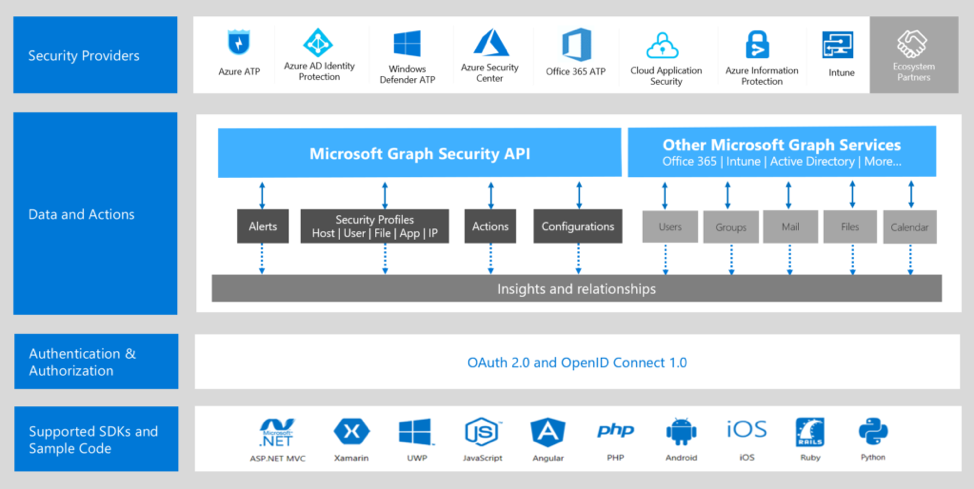
Microsoft has more solutions that create a valuable experience for his Microsoft Graph Security API: Windows antimalware platform, Windows Defender ATP, Azure Active Directory, Azure Information Protection, DMARC reporting for Office 365, Microsoft Cloud App Security, and Microsoft Intune.
Microsoft Intelligent Security Association (MISA)
Microsoft creates vast threat intelligence solutions. Microsoft collaborated with other companies to create a product under the name of Microsoft Intelligent Security Graph API. Microsoft calls the association The Microsoft Intelligent Security Association (MISA), an association that consists of almost 60 companies who share their security insights from trillions of signals.
- Microsoft products: Azure Active Directory, Azure Information Protection, Windows Defender ATP, Microsoft Intune, Microsoft Graph Security API, Microsoft Cloud App Security, DMARC reporting for Office 365, Windows antimalware platform, Microsoft Azure Sentinel
- Identity and access management: Axonius, CyberArk, Duo, Entrust Datacard, Feitian, Omada, Ping Identity, Saviynt, Swimlane, Symantec, Trusona, Yubico, Zscaler
- Information protection: Adobe, Better Mobile, Box, Citrix, Checkpoint, Digital Guardian, Entrust Datacard, EverTrust, Forcepoint, GlobalSign, Imperva, Informatica, Ionic Security, Lookout, Palo Alto Networks, Pradeo, Sectigo, Sophos, Symantec, Wandera, Zimperium, Zscaler
- Threat protection: AttackIQ, Agari, Anomali, Asavie, Bay Dynamics, Better Mobile, Bitdefender, Citrix, Contrast Security, Corrata, Cymulate, DF Labs, dmarcian, Duo Security, FireEye, Illumio, Lookout, Minerva Labs, Morphisec, Palo Alto Networks, Red Canary, ThreatConnect, SafeBreach, SentinelOne, Swimlane, ValiMail, Wandera, Ziften
- Security management: Aujas, Barracuda, Carbon Black, Checkpoint, Fortinet, F5, Imperva, Symantec, Verodin
MISA and Security Graph API
MISA is a combined security effort. It continuously monitors cyberthreats and fortifies itself. This enriched knowledge is accessible by Microsoft Intelligent Security Graph API. Azure Sentinel Fusion is the engine that uses graph powered Machine Learning algorithms. Fusion associates activities with patterns of anomalies.
Below you can see the Azure Sentinel Big Picture:
I hope you found this blog helpful and feel confident answering the question “what is Azure Sentinel”! As you can see, it’s just the tip of the Microsoft Security ‘iceburg’.
GAPS IN YOUR SECURITY POSTURE?
Work with AIS to identify security risks and gaps. Together, we'll create a plan for your secure cloud environment.