In a previous article, we explored using the CSI Secrets Store Driver and Azure Provider to mount an HTTPS certificate stored in Azure Key Vault on pods deployed to Azure Kubernetes Service (AKS). This was done using Linux containers and an ASP.NET Core application. But what about .NET Framework applications on Windows containers? Let’s see if we can take the same approach.
About Windows Containers
Containers initially grew out of the Linux world based on its natural support for container isolation using cgroups and namespaces. Therefore, Linux containers are usually the preferable choice when possible, such as for apps written on the cross-platform .NET Core 3.1 or .NET 6.0. However, many organizations have a significant investment in .NET Framework applications, which must run on a Windows OS. In this case, you may use Windows containers to deploy these applications to AKS, leveraging an organization’s investments in both existing applications and Kubernetes.
A few important things to note about Windows containers in AKS:
- The kubenet networking option is not supported on Windows nodes; therefore, you can use Azure CNI for the cluster. This requires additional planning and a larger range of IP addresses.
- The first nodepool in AKS runs system services and must use Linux nodes; therefore, creating a cluster for Windows containers is to make the cluster and then add a Windows nodepool.
- Your container image Windows OS version must be compatible with the node OS version. As of writing, AKS nodes are created with Windows Server 2019, so the to use for the .NET Framework parent images is 4.8-windowsservercore-ltsc2019.
See the AKS Windows FAQ for more information.
Using the CSI Secrets Store Driver for Windows Containers
Fortunately, AKS supports Container Storage Interface (CSI) drivers on Windows containers. Windows containers are also supported by the same CSI Secrets Store Driver and Azure Provider that we used for Linux containers and ASP.NET Core.
However, Windows is not enabled by default if you install using the Helm carts; you need to set the following configuration overrides to true:
-
windows.enabled
-
secrets-store-csi-driver.windows.enabled
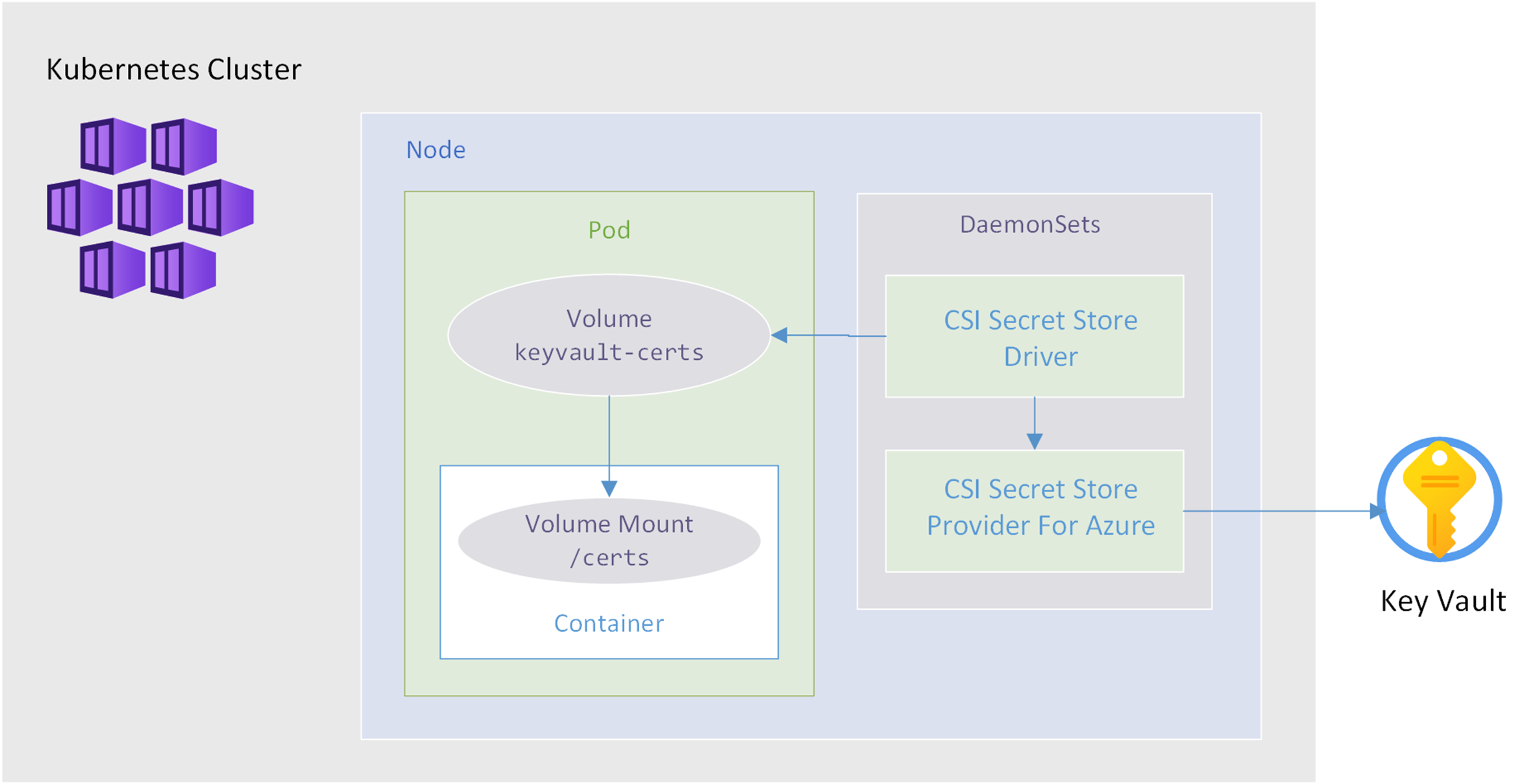
Once we have the driver and provider installed on our cluster, we can mount certificates stored in Azure Key Vault as files on our Windows container pods in AKS, just as we did for Linux containers.
The diagram below represents the flow from Key Vault to a pod and a volume mount on the container:
Configuring ASP.NET With HTTPS in Windows Containers
Running ASP.NET Core applications on Linux containers uses the Kestrel web server, and it is easy to configure Kestrel with the HTTPS certificate to use either through configuration or code. But ASP.NET applications running on Windows will use IIS as the webserver. How does this work on Windows containers, and how can we configure IIS in the container to use our mounted HTTPS certificate?
Looking at the Dockerfile used to create the .NET Framework ASP.NET image gives us a clue with this line:
ENTRYPOINT ["C:\\ServiceMonitor.exe", "w3svc"]
Its entry point uses the IIS Service Monitor app to run the IIS World Wide Web Publishing Service (w3svc).
So in our application’s Dockerfile we could set a new entry point that calls a script that:
- Install the mounted certificate file into the Windows Certificate Store.
- Configures IIS to use HTTPS with the imported certificate.
- Start the ServiceMonitor.exe process.
Here is a PowerShell example that expects the HTTPS_CERTIFICATE_PATH environment variable to be set with the certificate path:
$certFilePath = $env:HTTPS_CERTIFICATE_PATH Write-Host "Importing HTTPS certificate $certFilePath" $cert = Import-PfxCertificate -FilePath $certFilePath -CertStoreLocation Cert:\LocalMachine\My Write-Host "Creating HTTPS Binding" New-WebBinding -Name "Default Web Site" -IP "*" -Port 443 -Protocol https Write-Host "Binding Certificate to HTTPS Binding" Set-Location IIS:\SslBindings $cert | New-Item 0.0.0.0!443 Write-Host "Starting Service Monitor" C:\\ServiceMonitor.exe w3svc
Then in our application’s Dockerfile we copy in our startup script and set ENTRYPOINT the to call it, for example:
COPY ./Bootstrap-IIS.ps1 ./ ENTRYPOINT ["powershell.exe", "./Bootstrap-IIS.ps1"]
Finally, we can set the HTTPS_CERTIFICATE_PATH environment variable in our Kubernetes YAML to match the mount point and file name we configure the driver and volume mount to use.
Sample Repo
For a complete example with setup, configuration, and deployment instructions, see the aks-csi-keyvault-certs-win repo in GitHub.