In cybersecurity, quick response to incidents is crucial. Security engineers protect data and handle potential threats, but manual tasks slow them down. Microsoft Sentinel Playbooks automate these tasks, transforming security operations and enhancing an organization’s security. Let’s dive in and explore this game-changing tool.
Our Security Approach
AIS has extensive experience deploying Microsoft’s security solutions in Federal and Commercial Cloud environments, including implementing Microsoft Sentinel. Our Sentinel Deployment Framework empowers Security Analysts to deploy Sentinel effectively and optimize its capabilities. It serves as a guiding light for organizations to enhance security operations and maximize Sentinel’s potential. Refer to the figure below for key implementation phases and continuous improvement in incident response.
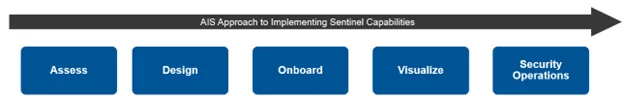
Figure 1 – AIS Sentinel Implementation Process
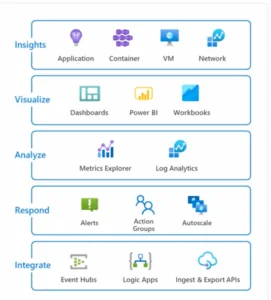
A well-functioning Security Operations Team (SOC) actively monitors and safeguards an organization’s digital assets. They promptly address security incidents and maintain overall system and data security. The diagram below highlights our key focus areas in Security Operations teams.
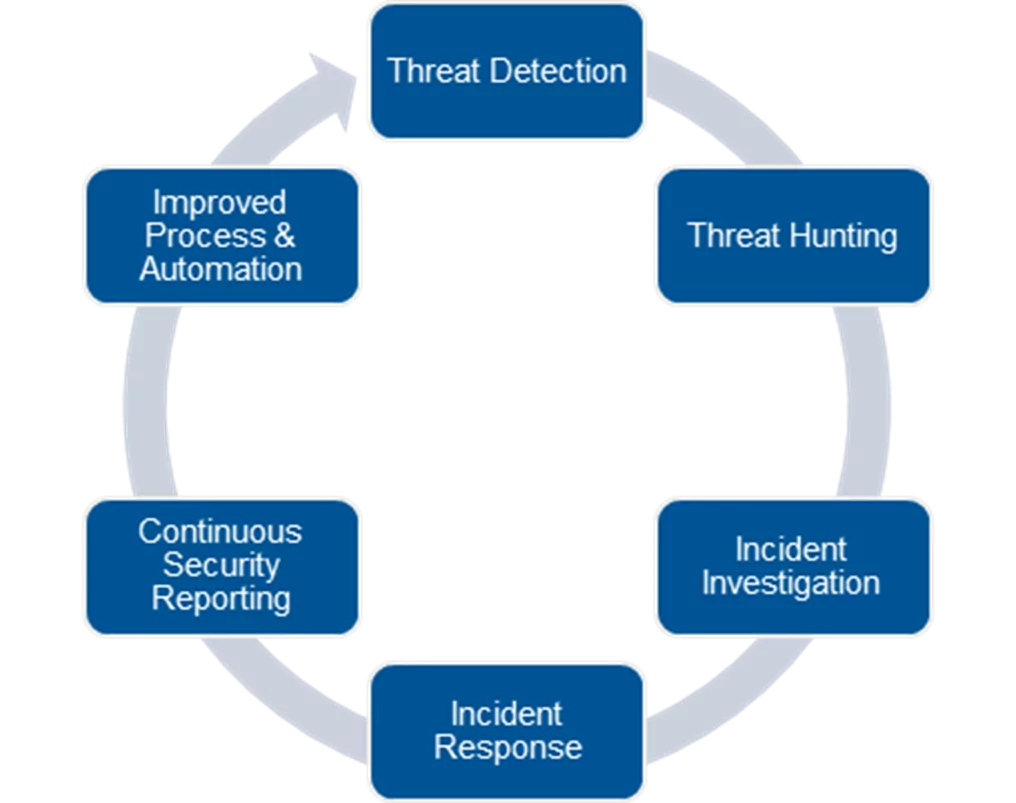
Figure 2 – AIS Sentinel Security Operations
Playbooks Value in Incident Response
Incident response includes key activities to detect and respond to security incidents. Automating these activities with Sentinel playbooks streamlines the process. The figure below illustrates a basic incident response process example.
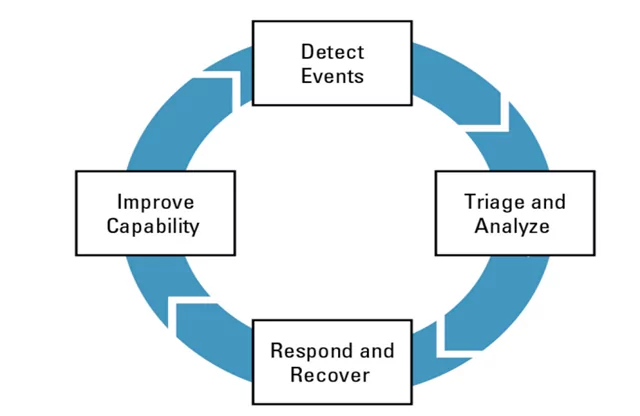
Figure 3 – Carnegie Mellon University CRR Supplemental Resource Guide
Sentinel Playbooks, built on Azure Logic Apps, are crucial in the Sentinel capability stack, saving time, improving efficiency, and streamlining incident response. By automating manual tasks, security analysts can prioritize complex activities, leading to faster and more efficient incident detection, response, and resolution. Key areas automated with Sentinel Playbooks include:
- alert triage
- data gathering for faster investigation
- evidence collection
- root cause identification
- threat mitigation
- system restoration
- control updates
- documentation
- reporting
- communication
Now that we have reviewed the value that Playbooks bring to our incident response tasks, let’s look at an example playbook.
Getting Started
To use Sentinel playbooks:
- Log in to Azure portal and go to Azure Sentinel.
- Explore the Playbook Gallery to find suitable pre-built playbooks.
- Choose a playbook that aligns with your needs and review its details.
- Configure the playbook to fit your environment and workflow.
- Validate the playbook by running it in a test environment.
- Deploy the playbook in your Azure Sentinel environment.
- Automate security tasks by manually triggering the playbook or setting up automatic triggers.
- Continuously check and optimize the playbooks based on feedback and changing requirements.
By following these steps, you can effectively utilize Sentinel playbooks to automate and enhance your security operations in Azure Sentinel.
Example Playbook
Playbooks can be manually triggered for specific incidents, alerts, or entities as needed. During an incident response investigation, all playbooks can be used to perform research and aid security analysts in deciding whether an alert or incident requires further investigation or can be considered harmless. The playbooks mentioned in this section are third-party playbooks that require API calls to access third-party services for conducting research on the evidence and entities mentioned in an alert or incident.
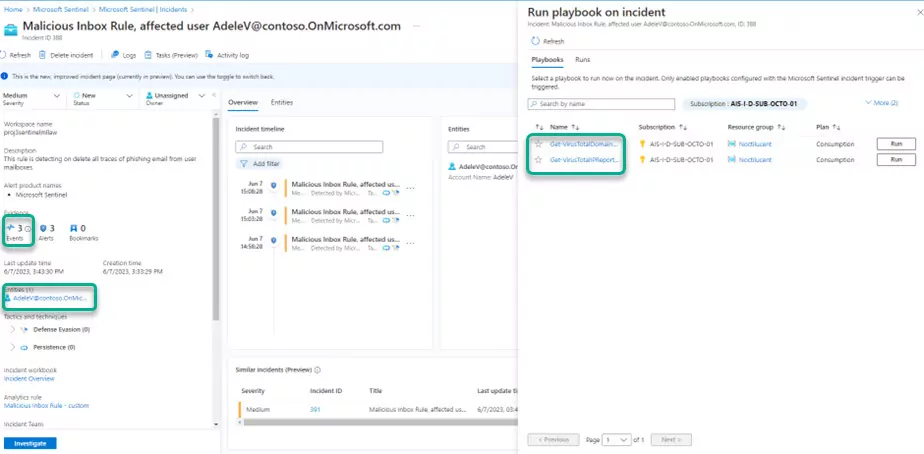
Figure 4 – Example Alert/Incident View
In addition, playbooks can automate and orchestrate the response process. They can be configured to run automatically when specific alerts are generated or when incidents are created or updated by being attached to an Automation Rule (“Tutorial – Automate threat response in Microsoft Sentinel”). This ensures that playbooks are triggered automatically when an alert or incident is received, providing security analysts with the necessary external research for their analysis. As a result, incident triage and investigation phases can be conducted more efficiently, leading to faster response times.
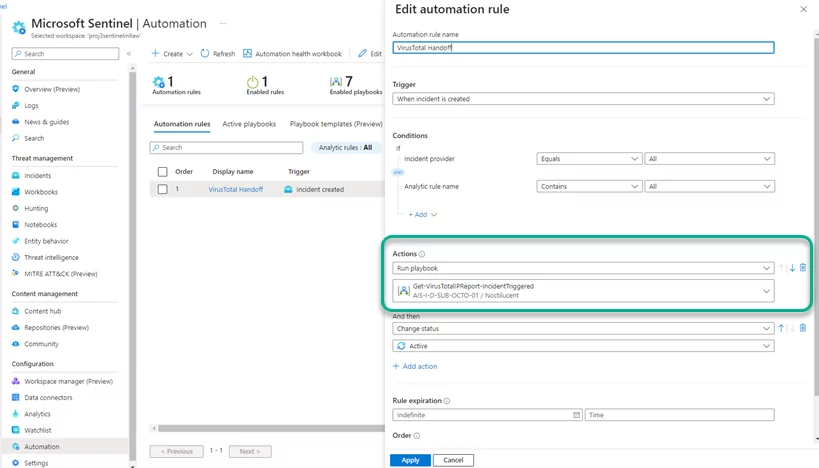
Figure 5 – Example Automation Rule
Our Favorite Starter Playbooks
Most of the Entities our analysts review are either emails, IP addresses, files hashes, URLs, and command line actions. These five entities cover almost all incidents/alerts generated by the Sentinel analytic rule templates. Based on our experience with Security Incident Response investigations and research tasks, we highly recommend using the following playbooks as they supply significant benefits:
- VirusTotal (VirusTotal Playbooks (GitHub))
- Get-VirusTotalDomainReport
- Used to research email domains
- Get-VirusTotalFileInfo
- Used to review hashes (Use SHA256 where possible)
- Get-VirusTotalIPReport
- Used to research IP Address
- Get-VirusTotalURLReport
- Used to research external URLs
- Get-VirusTotalDomainReport
- HaveIBeenPwned GetAccountBreaches Enrichment Playbook (HaveIBeenPwned (GitHub()
- Used to research if an internal individual’s email/phone has been compromised in earlier External Data Breach
- AI Commandline Analysis with GPT-3 Playbook (AI Commandline Analysis (GitHub))
- Used to research a Command Line entity
- Other Useful Playbook Templates in Sentinel for Tier 2 & 3
- Block AAD User
- Block IP
- Isolate Endpoint – MDE
- Relate Azure AD User Password
The screenshot below shows where Playbooks are in Sentinel and examples of the playbooks these 3rd party vendors can provide.
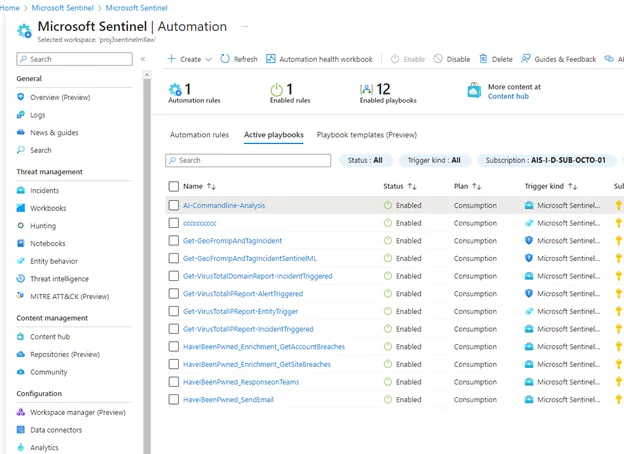
Note: Each playbook may have specific prerequisites, such as API Keys or associated costs. Please ensure that all necessary requirements are met before using the playbooks.
Tips & Lessons Learned
- Understanding Sentinel AAD Roles/Permissions: It is essential to grasp the Sentinel AAD roles/permissions needed for implementing/deploying Playbooks (Sentinel Contributor) and using them (Sentinel Playbook Operator).
- API Keys and Account Creation: Keep in mind that all tools referenced (VirusTotal, HaveIBeenPwnded, & ChaptGPT) used in Playbooks require API keys and some form of account creation, which may incur added costs.
- Cloud Tenant Compatibility: Playbooks have been extensively tested in Commercial Cloud Tenant, but it is important to review any differences or considerations for Gov Cloud Tenant.
- Analyst’s Role in Decision-making: Despite automation, it is crucial to emphasize that analysts still play a vital role in deciding the next steps for an alert/incident. Automation aids and augments their work but does not replace their ability and decision-making capabilities.
Key Takeaways
- Playbooks automate key tasks in Incident Response, reducing triage, research, and response times.
- Playbooks and Incident Response enhance proactive security by allowing analysts more time to process information from external sources, enabling better and quicker decision-making.
How AIS Can Help
If you have questions or want to explore our Security capabilities, contact AIS today. We are here to provide further information and support your security initiatives.