In today’s advanced Artificial Intelligence (AI) world, as significant advancements and benefits are happening, data breaches and cyber threats have increased exponentially also. The need for strong security measures has never been higher. Microsoft Sentinel is a Security Information and Event Management (SIEM) and Security Orchestration automation, and response (SOAR) tool that supplies rich and intelligent capabilities to defend and protect organization’s security posture in Microsoft Azure. By utilizing data connectors in Azure Log Analytics, Sentinel leverages its robust capabilities to analyze, troubleshoot, and mitigate anomalies within the customer environment. These data connectors enable the collection of specific events, allowing for a comprehensive approach to securing the customer’s data.
Microsoft Sentinel
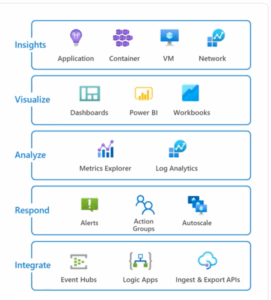
Microsoft Sentinel supplies several rich intelligent features such as Workbooks, Notebooks, Playbooks, Hunting, User and Entity Behavior Analytics (UEBA), MITRE ATT&CK, & Threat Intelligence for Threat Management. Workbooks supply dashboard functionality to support SOC (Security Operations Center) Analysts/Engineers to look at Sentinel data for Threat analysis. Sentinel Playbooks can be created to triage security incidents. Playbooks are Azure logic apps used to automate the process when a security incident occurs. Custom queries can be set up to trigger alerts when the threat condition occurs in Sentinel/Log Analytics. In addition, Sentinel provides the capability to trigger actionable alerts, initiate notification workflows, and apply necessary fixes as part of the mitigation process.
Follow Jorge Garcia’s blog post to learn more about Sentinel Playbook and how it can help with threat hunting and investigation.
Hunting and MITRE ATT&CK are implementations of custom queries applied to the data in the log analytics to continuously check the environment.
Azure Sentinel Notebooks is an innovative ML tool that revolutionizes cybersecurity by combining advanced technology with the convenience of notebooks. Security professionals and businesses can use Sentinel Notebooks to proactively hunt for and address threats, analyze vulnerabilities, and strengthen defenses. They are a game-changer in managing security operations, offering a comprehensive and efficient approach to protecting digital assets and ensuring a secure future.
Having gained an understanding of Sentinel’s security threat protection and an overview of Notebooks, let us dive into an example of Sentinel Notebooks and insightful lessons learned from our experience.
Sentinel Notebooks
Sentinel Notebooks primarily use Python for coding and offer extensive functionality for performing analytics using Python’s machine learning features. They also enable the creation of data visualizations with custom timelines and process trees within Jupyter notebooks. Notebooks can be run in the Azure ML environment or in standalone ML environment, as the Python libraries to connect to Azure Sentinel are embedded within each notebook. Azure ML environment will incur cost to run the compute cluster resources to run the notebooks. This blog post assumes that the reader is familiar with Jupyter notebook environment, how to configure and use MSTICPY Sentinel library to access incidents data in Azure. If you are unfamiliar with getting started, then follow Nisha Patel’s blog post to learn more about how to get started with notebooks using MSTICPY Sentinel library.
There are many built-in notebooks available in Microsoft Sentinel that can be used as it is or can be changed for security incident investigations. Follow this link to fast-track learning of Sentinel notebooks and become a Ninja!
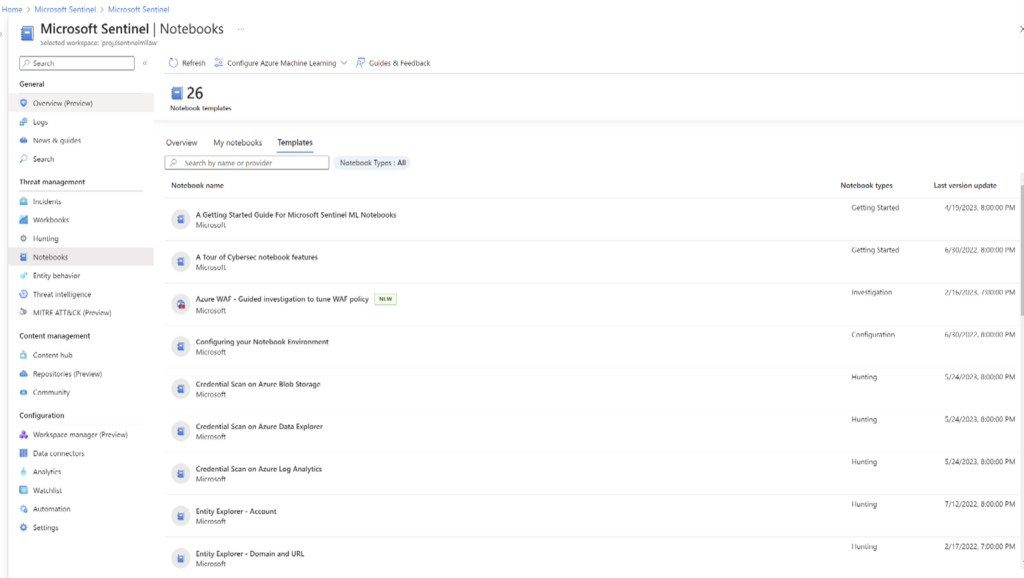
Figure 1 – Microsoft Sentinel Built-In Notebooks
While there are more built-in notebooks, we will focus on Guided Triage – Incidents and Guided Investigation – Fusion Incident notebook. I will share more details on what a fusion incident is, how the environment was set up to get a fusion incident, how does the notebook can help a security analyst.
Getting Started with Fusion Notebooks
Threats creates Security incidents and that can be configured to raise as Security alert. Security Engineers can analyze each incident separately, but it is impossible to correlate multiple incidents together to find a relationship or a pattern between some incidents without any additional tools. Incidents such as ‘impossible time travel’ is an example of a Fusion incident. It is impossible for the same person to log in from the USA and in UK at the same time. Microsoft Fusion correlation algorithm is smart enough to match attributes of these incidents to connect them together to identify the threat. Fusion incident is triggered by the correlation engine using ML algorithm. Fusion Analytics rule for Advanced Multistage Detection is enabled by default.
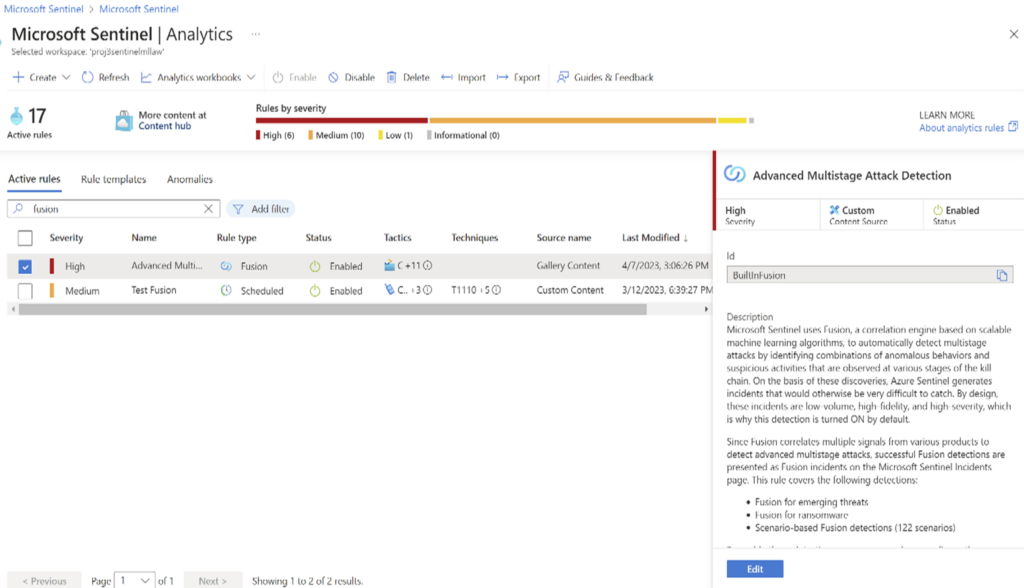
Figure 2 – Analytics rule to capture Fusion incidents.
Prerequisites
- Log Analytics
- Microsoft Sentinel
- Data connectors in Sentinel
- Logs data from various resources
- Configure Fusion (Built-in Analytics rule)
- Schedule Analytics rule
Generating Mock Data for Simulating Security Incidents
AttackIQ is a licensed product to create breach and attack simulation. You can assess it with a free demo trial.
Microsoft Security Architect Angelica Faber details out numerous ways to create mock threat data in her blog posts, Sentinel POC – Architecture and Recommendations for MSSPs – Part 3 – My Faber Security
New Ingestion Sample Data as a Service
Microsoft Partner link (Contains setting up Sentinel labs etc.)
Kusto Queries in Log Analytics
Once the AttackIQ simulates multiple attacks, multiple incidents occur. The built-in Fusion correlation engine finds the related incidents to form a Fusion incident.
SecurityIncident
| where RelatedAnalyticRuleIds[0] == (“BuiltInFusion”)
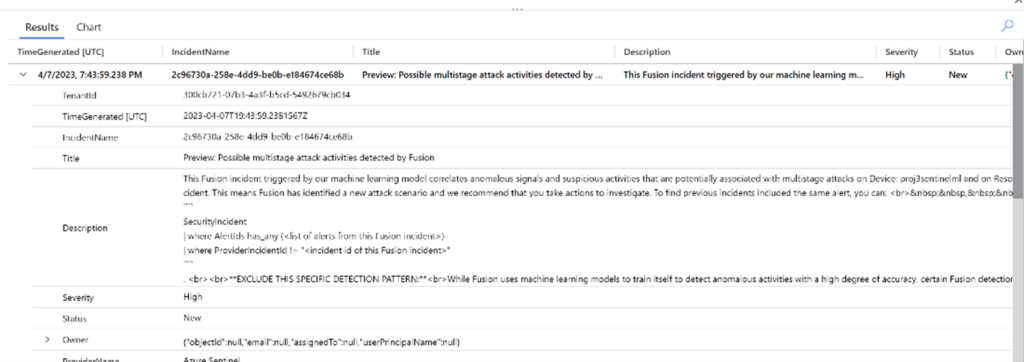
Figure 3 – Fusion incident shows up in the Log Analytics
Sentinel Notebooks
The following built-in notebooks help to investigate, analyze, and triage Fusion security incidents and other general security incidents. Having simulated attack data for security incidents to occur is essential to apply and run these notebooks to produce expected results.
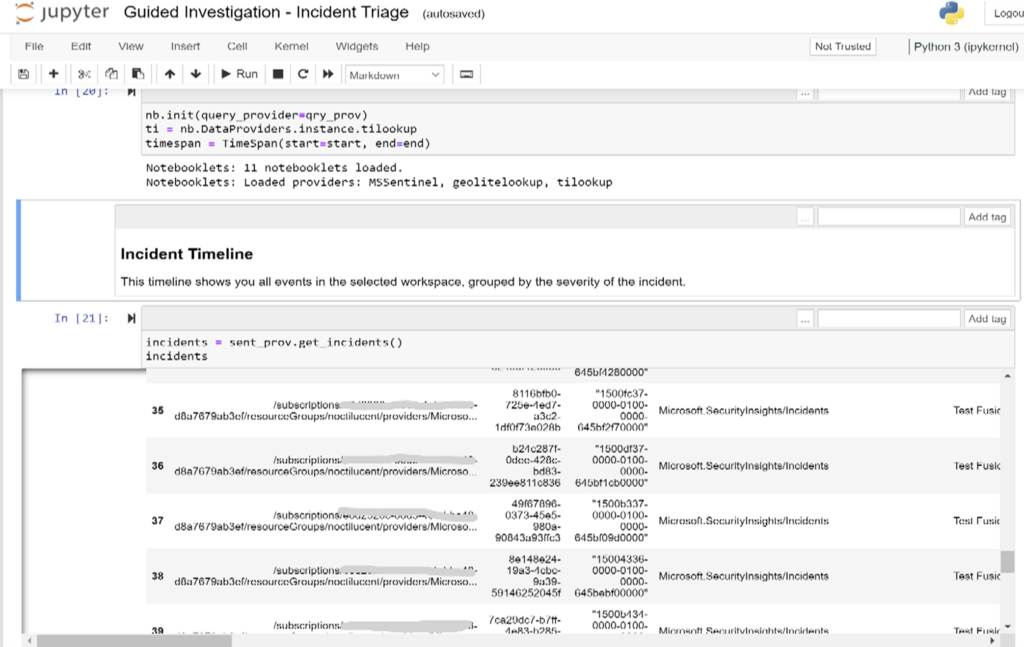
Figure 4 – Guided Triage – Incidents Notebook – Incidents occurred during the selected time range
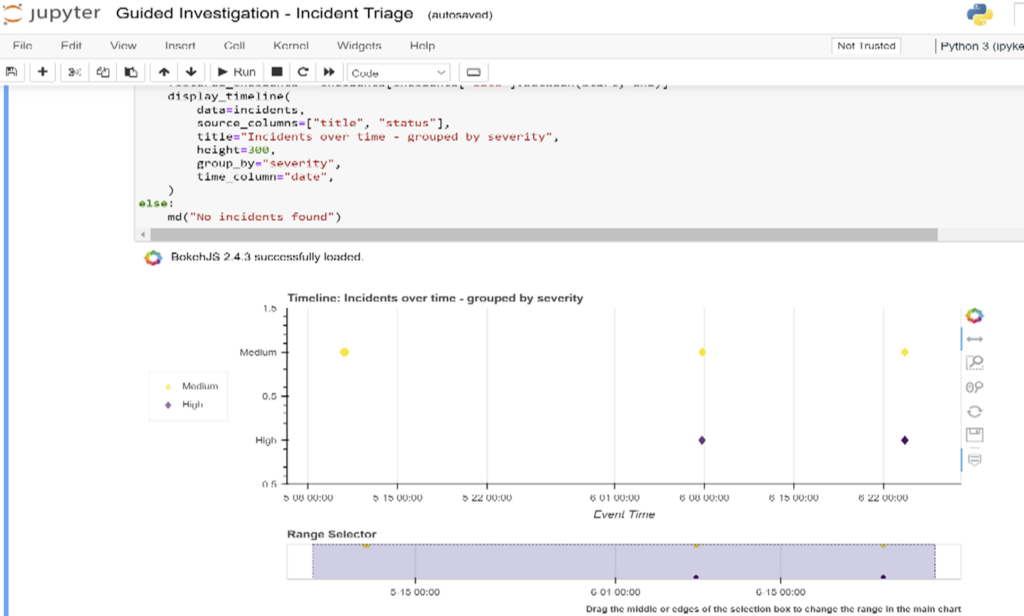
Figure 5 – Guided Triage – Incidents Notebook – Incidents are plotted using BokehJS library
I hope this blog post was beneficial in learning about Microsoft Sentinel ML notebooks and how it can support security engineers to analyze, investigate the Security Incidents and protect the customer Azure environment! Reach out to us to learn more and how AIS can help secure your environment!