The identity team of the internal AIS Microsoft Power Platform Hackathon delivered a flexible solution that could handle any of these use cases. Read on to learn how we did it.
Power Apps Portals are external-facing web applications that allow external users to interact with Microsoft Dataverse. It often serves more than one set of users, such as customers, employees, and partners. Therefore, it is critical to have a good authentication scheme and identity management for the Power Apps Portal applications.
Options Considered
We explored two authentication options to solve our app modernization challenge.
- Power Apps Portals authentication features
- Azure Active Directory B2C
Power Apps Portals provide a simplified experience to create and manage authentication settings and identity provider configuration. Besides providing access to internal users through Azure Active Directory, it supports various third-party identity providers such as Microsoft, Google, Twitter, Facebook, LinkedIn through authentication protocols like OpenID Connect and OAuth.
It also allows other authentication mechanisms such as SAML 2.0 and WS-Federation. All in all, it covers many use-cases of user access control to the portal application.
Azure Active Directory B2C is an Identity and Access Management (IAM) service that provides business-to-customer identity as a service. It enables customers and partners to use their preferred social, enterprise, or local account identities to get single sign-on access to business applications.
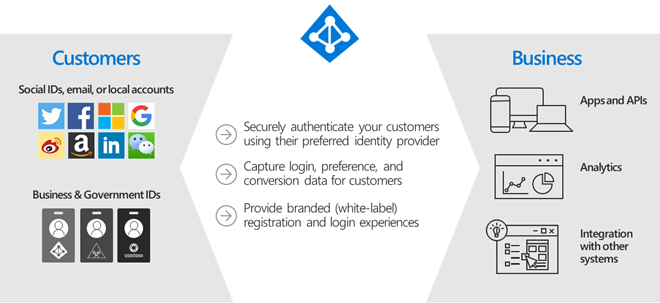
Rather than using Power Apps Portals authentication and managing a different set of user identities in the application, we chose to delegate this responsibility to AAD B2C. We made this decision because AAD B2C:
- Provides centralized change management
- Decouples identity from the application
- Has support for advanced security use cases
Centralized Change Management
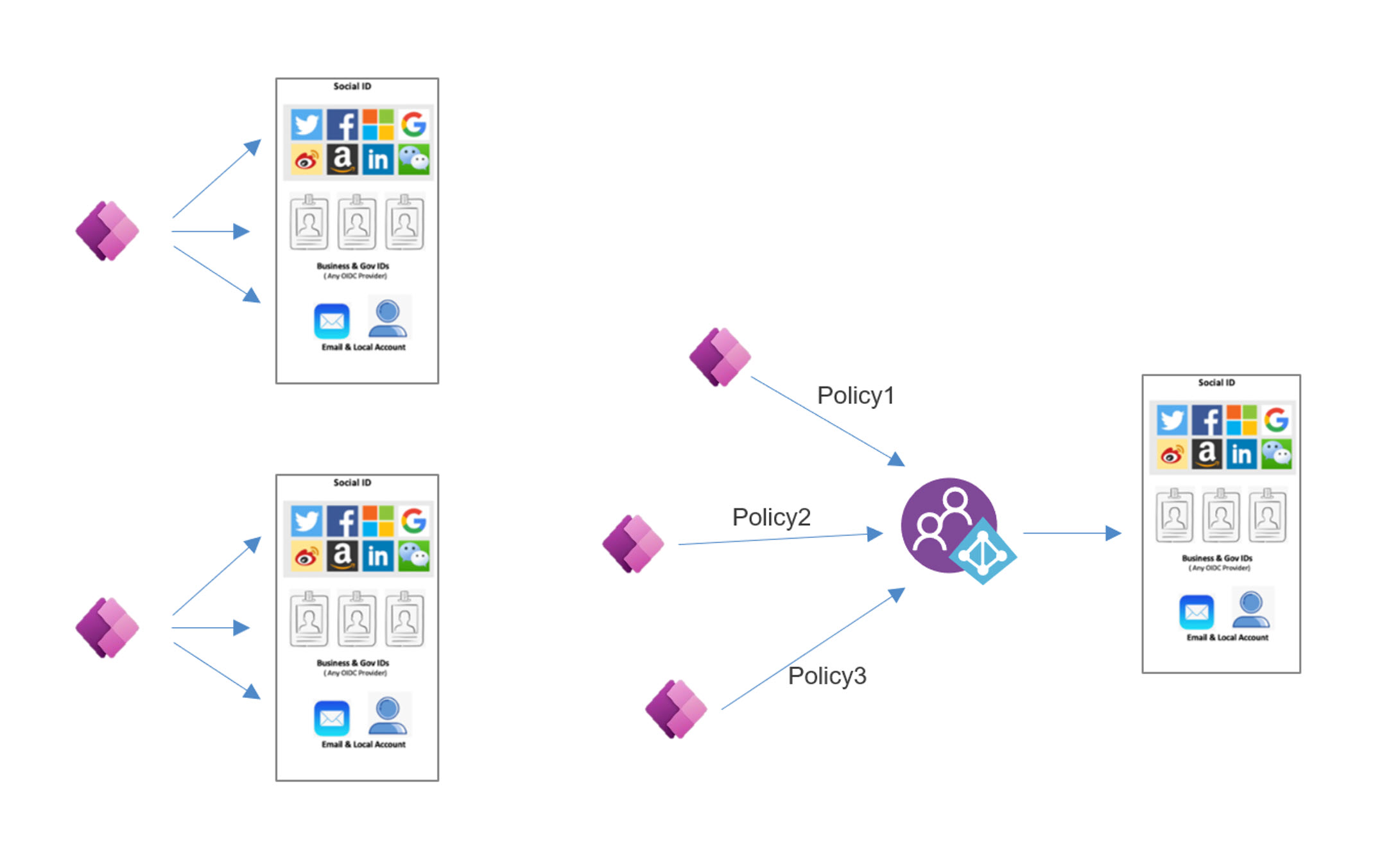
If every portal application configures authentication providers separately, it duplicates their effort, and managing different providers multiple times can be cumbersome. Instead, we can centrally configure the identity providers using AAD B2C. In addition, AAD B2C gives us the flexibility to make all changes concerning identity, security, and access control in one place.
If the security need of these applications differs, we can define them in custom policies. Applications with the same security need can reuse the same custom policies. This flexibility enables us to define and modify identity experiences with minimal to no changes to the applications.
Decouple Identity from Applications
Using AAD B2C removed the responsibility of user administration from the portal application. Decoupling IAM capabilities from applications mean the developers can focus on delivering business value. However, this does not mean the developers can ignore the security aspect of the application. Instead, it means IAM is a pre-condition to access the application, and it is being handled separately by the IAM provider.
As a single responsibility principle, developers should focus on applications, and security experts should focus on IAM. Power Apps Portal integrated with AAD B2C does just that.
JOIN OUR GROWING TEAM
Experience hackathons, boot camps, lunch and learns, and more at AIS.
Advanced Security Features
AAD B2C provides state-of-the-art identity and access management capabilities. Using Azure AD B2C as the authentication provider, we can leverage some of the advanced security features mentioned below.
Custom Policies
Custom policies are configurations that define the behavior of the AAD B2C tenant. We can use these policies to a custom trust framework for our organization. These policies can help to customize various aspects of our AAD B2C identity platform, including:
- A tailored experience for sign-ups, sign-on, profile & password management process
- Interact with each step in the login process.
- Set custom claim
- Custom validation of Technical profile.
- Integrate with external systems using REST API
It can improve organizational security by requiring end users to go through a workflow to use an additional authentication method. These policies also allow organizations to address security concerns on an application-by-application basis.
Conditional Access
This feature allows applications to fine-tune user access based on contextual factors such as user type, device, location, and session and then decide whether to allow, deny, or restrict user access. In addition, the conditional access feature provides high security to the applications that demand it. These policies give greater control over how and when our users access corporate resources.
For example, we can enforce a conditional access policy where users can access an application within a geographic region, but they need to provide multi-factor authentication (MFA) otherwise.
Identity Protection
AAD B2C also protects against risks by automatically detecting threats based on the always-on monitoring access behavior. The security teams will receive notifications whenever there are any suspicious activities. They can use automation and custom policies to block or restrict the access of such users. Applications protected with this feature will be more secure.
B2B Collaboration
Through AAD B2C identity providers, we can onboard multiple partners or vendors for business-to-business collaboration. We can securely share the enterprise applications with guest users from any other organization while maintaining control over their access. It works safely and securely with external partners, even if they do not use Azure AD. Whereas managing multiple B2B settings in the Portals app will be cumbersome, if not impossible.
Configuring Azure AD B2C Authentication
We used the techniques described below to configure AAD B2C authentication when modernizing our legacy application to MPP. At a high level, it requires two steps:
- Register an application in Azure AD B2C
- Use the registered application in the Portal app.
Registering an App in Azure AD B2C
First, we should create a new app registration in the Azure AD B2C tenant. We can use an existing app registration as well. Refer to this link for detailed instructions.
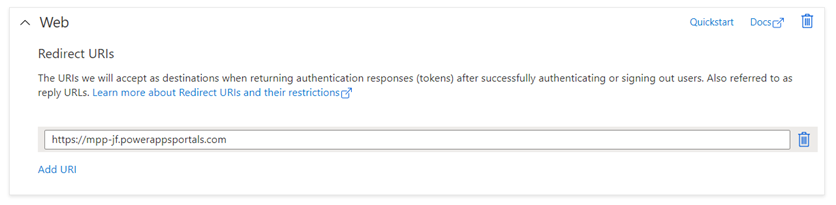
The app registration should be of a Web Type, and we should set its Redirect URI as the portal URL. We should then create a User flow for Sign-up and Sign-in. Optionally, we can create a password reset user flow as well.
After setting up these configurations on the Azure AD B2C tenant, we should have the following things handy.
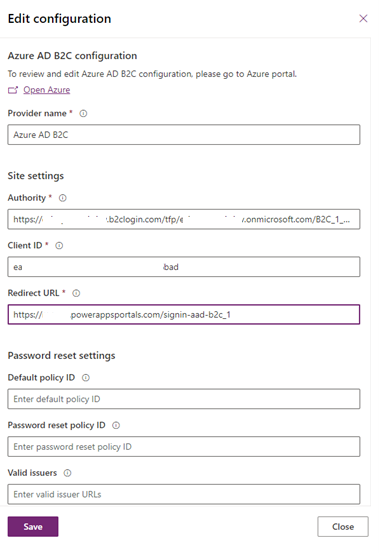
- Authority: The issuer URL defined in the metadata of the sign-in and sign-up policy flow
- Client Id: The unique Id associated with the application created in the Azure AD B2C tenant.
- Redirect URL: The URL where the Azure AD B2C will send the authentication response.
- Policy Id: The Id associated with the default sign-up and sign-in User flow.
Using the App Registration in the Portal App
After creating the application registration in AAD B2C, the next step is configuring our PowerApps Portal to interact with Azure AD B2C. We can select the portal application and navigate to the authentication settings and select AAD B2C as the provider.
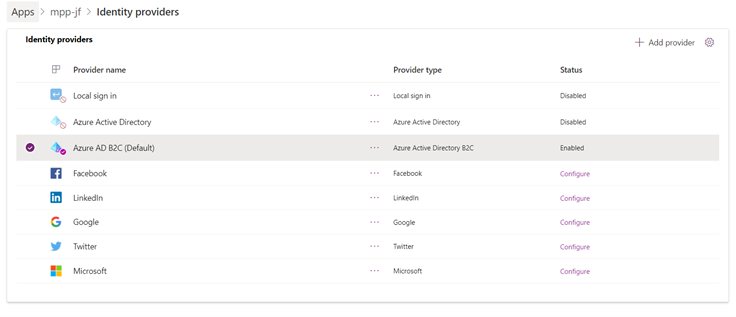
Save the authentication settings after setting the values collected from the previous steps (as shown in Figure 4). At this point, the portal application is configured to use AAD B2C for authentication. Refer to Microsoft documentation for more detailed instructions.
Conclusion
There are definite benefits of using Azure AD B2C as the authentication provider for portal applications. It provides seamless and centralized user access management with additional security features. At the same time, it decouples the business applications and their developers from the hassle of user access management.
Thank you to the Identity team for sharing their experience:
- Lav Kumar (team lead)
- Davood Khan