In today’s digital world, the threat landscape is increasing in both complexity and the level of sophistication in cyber-attacks. A new generation of attackers first targets the most vulnerable resources and then navigates to target high-value assets in an organization. Protecting individual areas like email or endpoints is not enough to be safe. XDR (Extended Detection and Response) is a new approach in the security domain that delivers intelligent, automated, and integrated security across domains to get ahead of attackers.
In this blog, we will see how Microsoft is helping its customers implement XDR with its series of products known as Defender products.
So, what is XDR and how it works? XDR centralizes the threat tooling stack to get control over security. It includes network analysis, integrated threat intelligence, machine learning-based detections, and investigation response orchestration.
Recently, Microsoft unified all XDR technologies under the Microsoft Defender brand, and it is the most comprehensive XDR available today, preventing, detecting, and responding to threats across identities, endpoints, applications, email, IoT, infrastructure, and cloud platforms. It includes new features such as multi-cloud (Google Cloud and AWS) and multi-platform (Windows, Mac, Linux, Android, and iOS) support.
The following image shows the re-branded Microsoft Defender products.
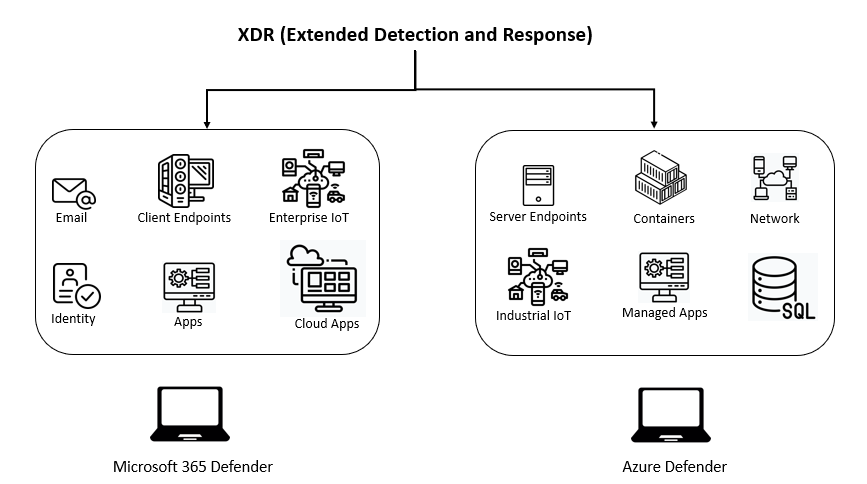
As shown in the above diagram, anything that exists in a modern workplace suite is protected by Microsoft 365 Defender, and anything that exists in Azure is protected by Azure Defender.
Now let’s understand how this re-branding helps with XDR and why this branding has been done.
Microsoft has a list of defender products in its Catalog like Microsoft Defender for O365 used for detecting and response emails, Microsoft Defender for Endpoint used to detect and respond to endpoints, Microsoft Defender for Identity used for detecting and responding to identities, and more. The core capabilities of all Defender products are in detecting and responding to a threat that has been detected already. So, this is the core functionality of DR.
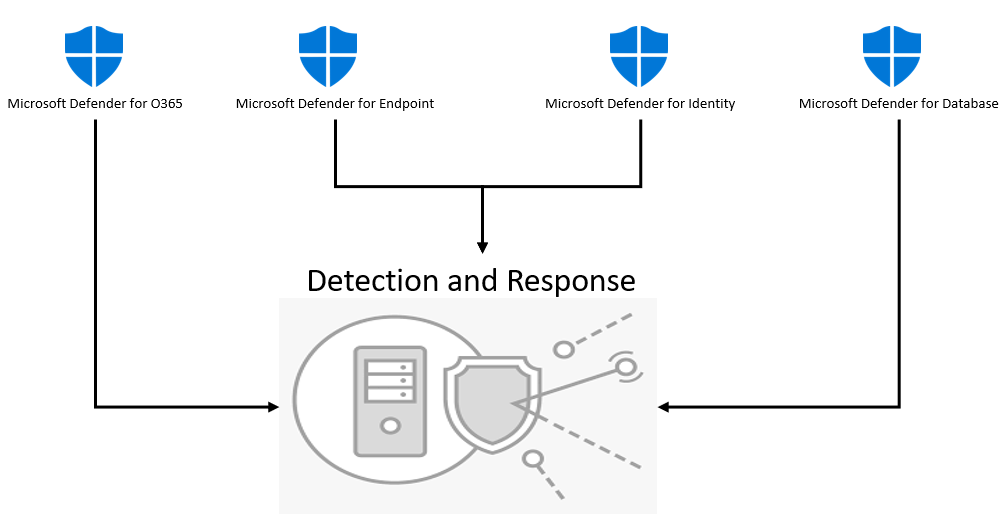
Now, let us see a use case of how threat detection in unified XDR works.
Assume Microsoft Defender for Endpoint highlighted a threat indicator, since all services are grouped, this indicator will be shared with other defenders. On the other hand, if we have different security solutions, the biggest challenge we will be facing is all security products are connected and the threat is shared across products. This is a great advantage of using Microsoft XDR which shares threat indicators across defender products out-of-the-box. This makes sure that we are protecting our digital states end-to-end. This is what makes up Extended Detection and Response (XDR) capability. Here “X” can be any security solution.
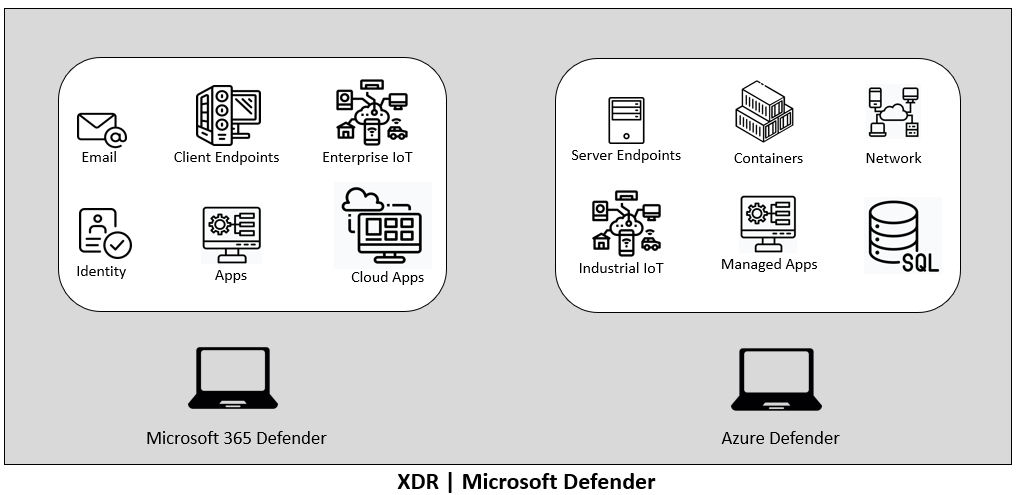
When we combine M365 Defender Suite with Azure Defender Suite, everything is protected, and the threat intelligence is shared across security products. This is the baseline of Microsoft XDR capabilities.
Interested in learning more? Reach out to AIS today and we can help your organization in understanding and adopting Microsoft Defender products.